Is Secure Development Lifecycle about the Code?
We help software development companies secure their software development practices: design, testing, deployment and infrastructure and put the “Sec” in DevSecOps
Secure Development Life Cycle Consulting
There are many best practices, frameworks, guidelines, checklists and books about secure software development, but we are the ones who will help you to develop secure products
9 areas to Develop
14 DAYS
1 INFORMATION SECURITY ASSESSMENT
Forget the boring reports you have seen. We develop a complete Information Security Program for you, with detailed steps to follow for your technical team. We have done this for banks and nuclear power plants – it is your turn to go through our assessment!
Password & Access Management
People store passwords everywhere and reuse their online shopping password for their corporate email! To top it off, their password is P@ssword123 or its variation and is guessed in 5 minutes. We help discover all such practices.
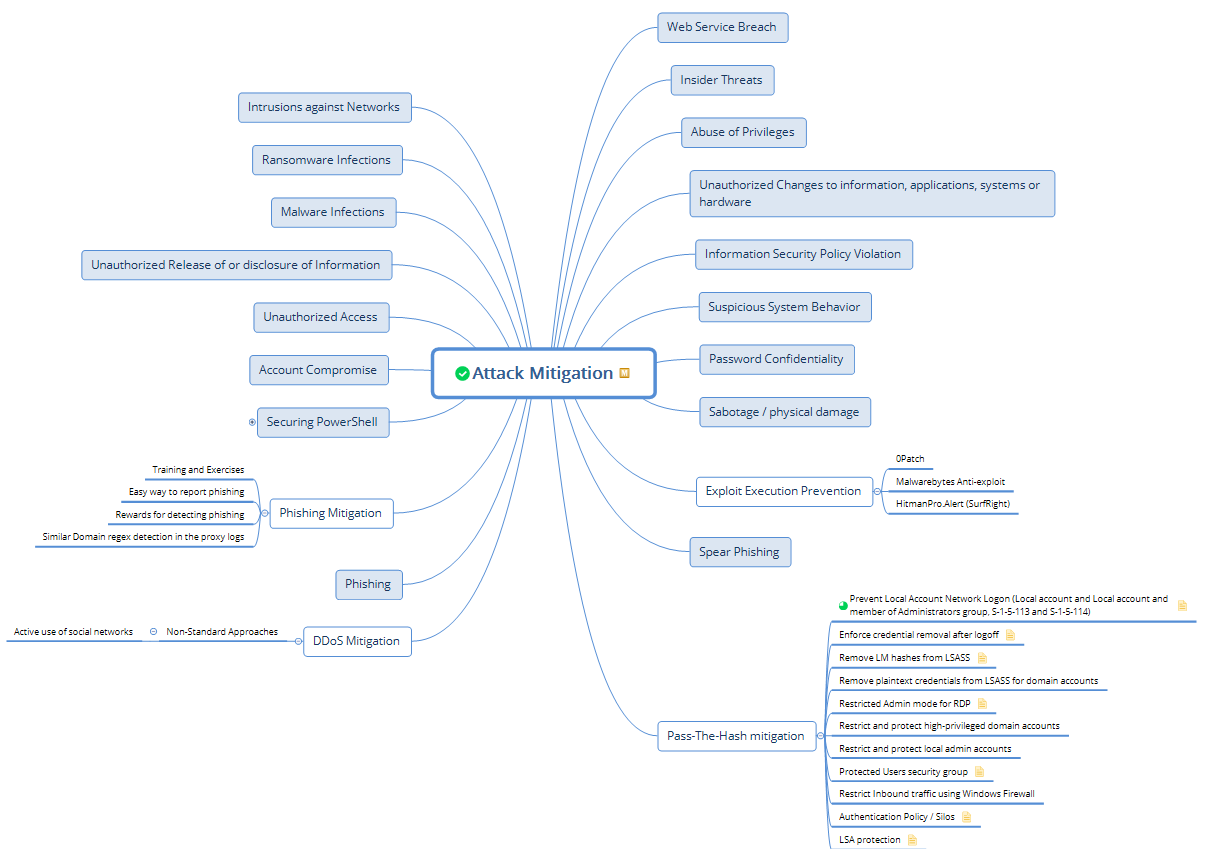
Attack Mitigation
We check for existing mitigation controls for 17 types of cyber attacks: account compromise, unauthorized access, ransomware, network intrusions, malware infections, sabotage, security policy violations, etc.
Security Awareness Training
We will check what is the effectiveness of any existing security awareness efforts in the client's business.
We will also find all business areas where the employees are particularly vulnerable to social engineering attacks and in need of additional specialized training.
Cloud Security Architecture
Microsoft 365 has 280+ security settings. Amazon Web Services and Azure have hundreds of security configuration options, too - we will discover and document all security improvement opportunities in your cloud infrastructure.
IT Infrastructure Security Assessment
We help our customers discover weak security configuration in their IT infrastructure by checking Server & Network Device Hardening, Desktop Hardening, Network & Web Service security, Data Security, Backups, etc.
Vulnerability management
How many vulnerable machines / apps do can a company have in their network?
We help our customers establish and manage a Vulnerability management program which will gradually reduce the vulnerabilities in their network.
Email & Communications Security
Getting access to a corporate account may grant a hacker access to all internal systems, too. We protect our customers by implementing secure authentication, ensuring the integrity and confidentiality of your communications.
Penetration Testing
Breach simulation is an integral part of every Information Security Program. Our customers can rely on us to support them in the initiation, execution and conclusion of a Penetration Test.
Secure Software Development
Software development should be a rapid and efficient process. We help our customers integrate security into the design, development, testing, integration and deployment of their code.
Security Policies and Procedures
Policies and Procedures are the governing laws of a company's business. The ones we create are living and breathing documents bringing order and structure to our customers' security practices.
Secure Remote Access
Secure Work From Home is one aspect of remote access, but we also take care of third party partners and outsourced employees, vendors and guests. Remote access to data is not limited to VPN.
Zero Trust Networking
And this is exactly why we expand your defenses beyond VPN and add Zero-Trust as your main principle of defense.
Advanced Endpoint Security
Antivirus is just one of 12 controls we implement to defend endpoints from advanced hacking attacks. We prevent the exploitation of these devices via malicious documents, scripts, 0day vulnerabilities and more.
Security Monitoring
We will help you transform your IT infrastructure security by implementing Server & Network Device Hardening, Desktop Hardening, Network & Web Service security, Data Security, Backups, etc.
Plus much More
Every Information Security Program we build and execute for our clients is different. Their teams, infrastructure, applications used and business objectives are differ and we often expand our services to serve them better.
Step 1: Secure Development Assessment
The only way to map a customers’ security journey is to assess where they are and where they want to be in a year.
- We assess your current security controls in every one of the 14 areas above and find the critical items which pose the greatest, immediate risk of a security breach and generate a plan to rapidly close the gaps with compensating controls.
- We also find the medium-rated and low-rated vulnerabilities and missing controls and include them in the Information Security Program Plan that we create for you as an output of the assessment.
- We then utilize the Information Security Program Plan as a list of objectives and help your team achieve every single one of them within a year.
Step 2: Secure Software Development Implementation
The output of the Information Security Assessment is a detailed report with deeply technical step-by-step recommendation, but the real value of the assessment is in the Information Security Program Plan you will receive.
- Regardless of who manages your information security, they will be able to follow a strategic, business-priority following plan to mitigate all findings discovered during the Information Security Assessment within just 12 months.
- We also find the medium-rated and low-rated vulnerabilities and missing controls and include them in the Information Security Program Plan that we create for you as an output of the assessment.
- We then utilize the Information Security Program Plan as a list of objectives and help your team achieve every single one of them within a year.
Secure Software Development Practice Stages
Our Identity and Access management service It is part of the CISO as a Service and is an ongoing effort throughout the entire time we work with our customer. During that time, we identify all business assets and all people having regular or administrative access to them. We also identify potential ways to attack or misuse the access and come up with compensating controls for them.
A critical part of this project is to educate the whole team of the customer on the importance of not reusing passwords and how to use a password manager efficiently.
An important objective to achieve with any customer is reaching passwordless authentication – something we achieve with a combination of services from Google, Microsoft, Yubico and utilizing biometrics and physical security.
Attack Mitigation
Every company has a different threat landscape due to the data it holds, its customers and competitors and the resources it operates with.
Due to this, there are different attack methods hackers can use to compromise the security of the company and achieve their objective – to steal money directly from the accounting department, to steal confidential data or even hold the company for ransom, as it happened with this famous law firm security breach.
We take all of this into account, but we also cover the fundamental types of attacks with all our customers:
- Intrusions against networks
- Ransomware infections
- Malware infections
- Unauthorized release or disclosure of information
- Unauthorized access
- Account compromise
- Abuse of privileges
- Unauthorized changes of information, applications, systems or hardware
- Information security policy violation
- Suspicious system behavior
- Password confidentiality breach
- Sabotage / physical damage
- 0-day exploitation
- Phishing attacks
- Spear Phishing attacks
- Web service breach
- Insider threats
We come up with compensating controls for all of the above and implement them for our customers depending on business priority and risk.
Let's get to work together!
We serve very few clients and take pride in our work. Can we become a great team and achieve amazing things together?