We will cover much more than just a list of cybersecurity consultant companies. How could that work out in your favor if you didn’t know how to select one?
Hacking teams use complex sets of techniques, which cannot be defeated by simply getting a bunch of security products from a reseller:

This is why working with your IT team or IT company to improve your cybersecurity will not be successful in defending against advanced hacking teams. Because of the complexity depicted above, you need specialized cyber security consultant companies.
Fighting this swiveling, upgrading, evasive criminal machine requires the skills of entire teams of experts – and if the hackers are already attacking you, you’ll need cybersecurity consultant companies to help you.
They generate and work on Information Security Programs like the one depicted below:
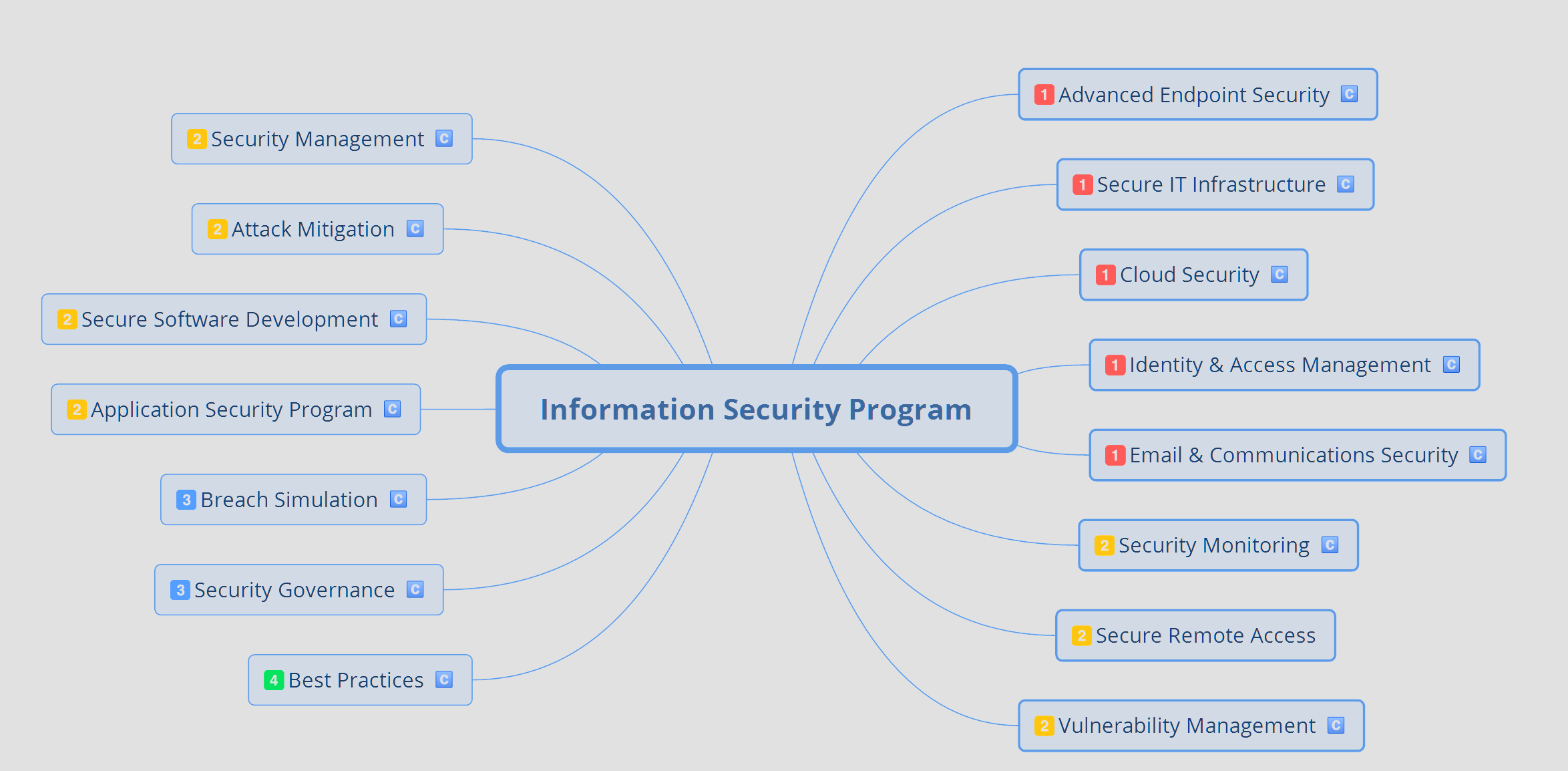
Each element listed above contains two to twelve levels of depth. That is why security consultants are in high demand and hard to find!
In addition, security consultants help IT teams work on and improve their cybersecurity architecture, like so:
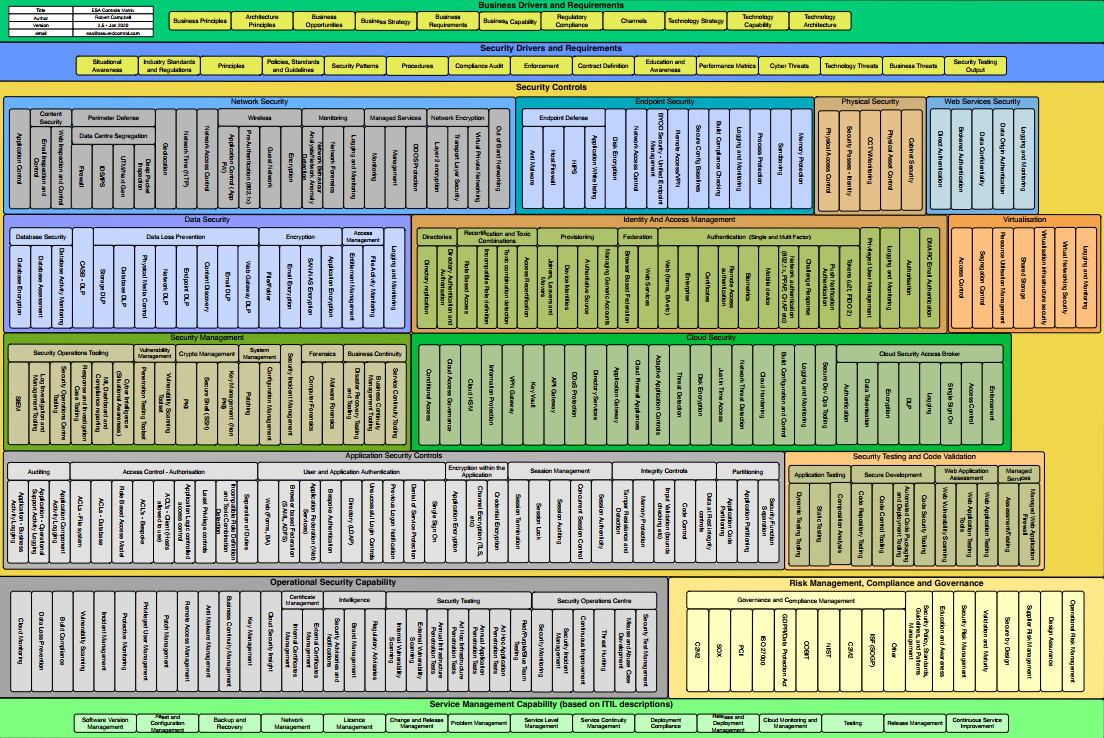
We know how to use our expertise to help streamline IT operations and ensure that your business machine keeps churning out high rates of return for many years to come. Security is not just about defense: it is about efficiency, reducing human error, reducing risks, thus increasing revenue and as a final touch, a higher valuation for your entire business. Cybersecurity also helps improve customer trust and market share.
The purpose of this article is to help businesses choose the right cybersecurity consultant company. And for that, just showing you a list of companies is not enough, because you will not know the criteria to pick one. Is it the price? What if their prices are similar? Is it location? Skill? How would you determine their skills, just by speaking with a sales person?
Understanding Your Cybersecurity Needs
“If you don’t know where you want to go, then it doesn’t matter which path you take.”
― Lewis Carroll, Alice in Wonderland
Just as you can’t prescribe medicine or operate on yourself in a medical emergency, you shouldn’t try to diagnose your cybersecurity risks and problems. Call a cybersecurity company and discuss this with them. During that call, they will ask about your current IT infrastructure, IT practices, projects, software in place, and plans for changes in the future. They will propose a plan following your answers and their expertise.
Assess your business’s current cybersecurity posture.
A better approach would be to run a cybersecurity audit of your company against an industry standard such as SOC2 or NIST 800-53 v5. This audit will take 3 to 5 days for data collection and up to two weeks to produce your Information Security Program plan. Then, your chosen cybersecurity consultant will help you prioritize any fixes for all the security gaps found during the audit.
Identify specific cybersecurity challenges and vulnerabilities.
Some vulnerabilities could be exploited remotely by even unskilled hackers, which should be remedied immediately. Every company has them, especially the ones that are just starting on their cybersecurity journey.
Determine your budget and resources for cybersecurity consulting services
We have found that many of our clients can sell their products and services more easily after becoming secure. You could look at this from a business development perspective: if you spent a certain amount of money on cybersecurity and this allowed you to stand out from your competition, how much would it be worth to gain more market share? How much market share would you lose if suddenly most of your competitors started caring about cybersecurity and you didn’t? This puts the budget into a whole new perspective.
Key Factors to Consider When Choosing a Cybersecurity Consultant Company
Expertise and Specializations
Reputation and Track Record
Reviewing case studies and success stories of past projects from their website should be easy.
Certifications and Accreditations
Verify the consultant’s accreditation with relevant regulatory bodies, if relevant.
Approach and Methodology
– Evaluate their methodologies for risk assessment, threat detection, and incident response
Communication and Collaboration
Your cybersecurity consultant will often work with various departments within your company. They will have to speak without technical terminology and explain the risks without causing unnecessary panic in case of an incident. Asking them directly about it may not be the best idea – ask them to explain what “phishing” is and note their reaction and explanation.
Tips for Making the Final Decision
Conduct in-depth consultations and ask the right questions
You don’t have all the time in the world. Pick one aspect of your business – such as email and collaboration – and drill down the potential solution providers on their approach to protect you. After a few interviews you will get an in-depth understanding of your own problems
- Obtain detailed proposals and cost estimates
- Negotiate contract terms and service level agreements (SLAs)
- Seek references and conducting background checks
- Trust your instincts and choosing the company that aligns best with your business goals and values
- Recap of key points covered in the article
- Encourage for businesses to take proactive steps in securing their cybersecurity infrastructure
- Reach out for further assistance or consultation if needed
A List of the Top Cybersecurity Consultant Companies
If you came here for a list of companies, here is a list. Although I hope you read the advice above first:
- Yours truly, Atlant Security
- For larger government or military contractor needs, contact BAE Systems
- For large government projects involving auditing and compliance, PwC
- If you are a large enterprise in need of a bunch of security solutions from a single vendor, go for IBM Security or
- If your digital life revolves around Microsoft, definitely try out their consulting services (Alexander, the founder of Atlant, once worked for that team)
- If you live in the Google universe, try out Mandiant Security Consecastulting
- For pentesting, vulnerability management, and complex security programs for larger companies, you can work with Rapid7
- If you experience constant cyberattacks against your email systems, there’s nothing better than Mimecast
- For managed detection and response, you should try out Binary Defense
As always, with so much information, you might feel overwhelmed. Feel free to contact us; we will do our best to help you.



