In this webinar, we show you how to protect your company from ransomware attacks without buying ANY security products.
All we focus on is proper security planning, applying the right security settings to your Operating Systems and software (security hardening), and implementing the right security practices – identity and access management, policies and procedures, etc.

Real-life attack scenarios
I’m going to cover one major incident, and I think many security vendors like this incident and like to talk about it.
I like it because of its impact and because of its clear timeline.
We could speak about modern prevention of modern incidents in cloud systems, however, I think 99% of all of you today work in an infrastructure that has Active directory as its core.
I’m going to talk about securing Active Directory mostly and then if you have questions about preventing Ransomware attacks in cloud environments, I can answer them if we have time.
Now my favorite slide of the whole webinar: please take a good look at this slide!
Because this slide has been with me for years and years and I’ve been showing it to so many people everywhere I worked at.
It’s a very old slide taken from a New Zealand security conference, I think it’s open-source that’s why I’m using it – it’s available on their GitHub.
Basically… hackers don’t give a shit about what you have in your network, they are like water: they find a way through the smallest cracks and they don’t care if you have the budget, if you have the team or if you have legacy systems: they just don’t care.
If we look at a generic security incident which is what a ransomware event actually is, you will see that normally the timeline goes like this.
Hackers have projects, they have project managers, they have organized groups and they have like Kanban boards, they have monthly objectives and KPIs just like all of us and they do their research and their research follows very strict rules and is very structured and very organized as well.
A hacker’s research process is not much different from the process of investigating cybercrime and their process looks at your people and your technologies.
They might look at the job opportunities you advertise to see what kind of technologies do you use and their research is so rigorous that usually, they find the vulnerabilities in your infrastructure
better than you can find them.
This happens, because you’re busy with all kinds of tasks that your boss gives you and the hacker is only looking for vulnerabilities in your organization for a while, sometimes for months or even years, depending on the payback.
As you can see on that slide, the time it takes between the initial breach and them achieving a foothold in your company is around two weeks.
Then it takes them between five minutes and a day to become an admin in your organization and becoming an admin on one workstation often is the same as becoming an admin on the whole domain level.
I’ll explain later why.
Usually, they stay undetected for months, sometimes they stay undetected forever, not for years. And the average time is four months.
Average usually means between zero and infinity, so an average of four months basically means nothing: they can stay forever in your network if you don’t detect them.
What happens then?
When we prepare for a Ransomware event, usually most companies trust a security vendor. They buy some kind of fancy EDR or a fancy security solution on the blockchain, and Nextgen or whatever someone convinced them to buy and the result is usually this one:
We see all these major breaches happening and don’t you think that all of these companies on the screen had an antivirus or an EDR or a security monitoring solution?
All of them had security teams and all of them got hacked.
Why?
Because in the majority of organizations, I would say more than 90 percent of organizations you see someone buying security solutions but you don’t see people doing security architecture correctly. You don’t see people doing security hardening right and today’s webinar is all about security architecture. It’s all about security hardening.
If you look at this ransomware attack which happened against a network of hospitals and shut down multiple hospitals (I chose this because it’s a great example of a ransomware attack) and please
focus on where the attack happens!
You will see that from the initial foothold when the attacker gained some kind of execution on a single workstation in a single hospital, it took them just a few days to gain persistence, which means, when you reboot the workstation, the hacker will still be there and then they stayed on for several weeks before they deployed their ransomware attack.
And if you look at the timeline, you will see that the hacker moved from one hospital to another and from network to network, they gained administrative access in the whole enterprise network across several domains and across several Active Directory domains, and just when they were detected and they knew they were detected because obviously, they are monitoring your communications and emails and know when you start the incident response process.
Ransomware is NOT a security incident!
Please remember, that ransomware is not a security incident. Ransomware is just the point when the hacker wants to do two things: profit or hide their tracks.
If they encrypt all your computers in the whole organization, you cannot recover evidence and you cannot recover your data, because encryption is very solid, encryption is like math, you can trust encryption just as you can trust the math behind it.
Before the incident, they usually see all your internal communications they see, if they are detected and you have started investigating the breach and the moment the investigation starts, they have a very short opportunity window, because before they are kicked out and that’s usually the moment when they do the ransomware.
Before the ransomware event, they take all your data, they download all your data so that they could extort you with your data if you decide not to pay. So the ransomware event is not the security incident, the ransomware event is a symptom of the sickness it’s not the sickness itself.
Ransomware is not a virus it’s not a kind of malware, ransomware is a group of people.
Think of ransomware as a team. So you’re not fighting technology, you’re not fighting malware, you’re fighting a team of hackers inside your network, who decided to use ransomware for one reason or another.
How do you fight them?
Please have backups. But remember, these people are in your network for months, and if they’ve been in your network for months, then you can’t really rely on your backups because the hackers have the same system privileges as your domain admins in most cases. And they have the same administrative rights and they have the knowledge to disable your backups or corrupt your backups in such a way that you couldn’t rely on your backups.
If you can rely on your backups, all their work for months is wasted, because you can just restore and not pay them anything.
So work hard on your backups.
You can even build some or buy some data diodes, which will enable one-way backups to avoid their corruption or deletion.
I’m not going to focus on backus, because this webinar is about prevention and backups should have been a part of your disaster recovery plan. Something you should have worked on for months to get it right.
People, Process, and Technology solutions to the ransomware problem
You should work on building your processes and educating your users, but this webinar is about technology and technological defenses that you can apply today to take care of the ransomware problem, or to be more precise – the security incident problem, which precedes ransomware attacks.
If you just start buying security products in order to protect from ransomware, you will end up with a lot of products having nice flashing lights and not much security or functionality.
This is because configuring an enterprise security product can sometimes take months or even years. Some products require constant tuning and configuration and can never be seen as fully configured.
One of the core values of Atlant and of this webinar is that 20% of the effort usually delivers 80% of the value. So this webinar focuses on exactly that: the actions you can take to obtain the fastest and strongest improvements to your defenses in the shortest amount of time. All without buying a single commercial security solution.
Which 20% of your security efforts should you do, to get 80% of the defense benefits?
Defending the patient zero workstation
If you don’t defend the patient zero workstation, unfortunately, you will fail to defend your organization. Any security product which doesn’t solve this problem will not solve the security incident
the problem, so let’s focus on the patient zero workstation, or the Endpoint, as in, ANY endpoint.
Because, if the hackers cannot get a foothold in your network, they will simply choose an easier target.
That’s just how it is:
Become a difficult target!
There is an amazing tool, which is available on GitHub, it’s free of charge and open-source: Hardentools
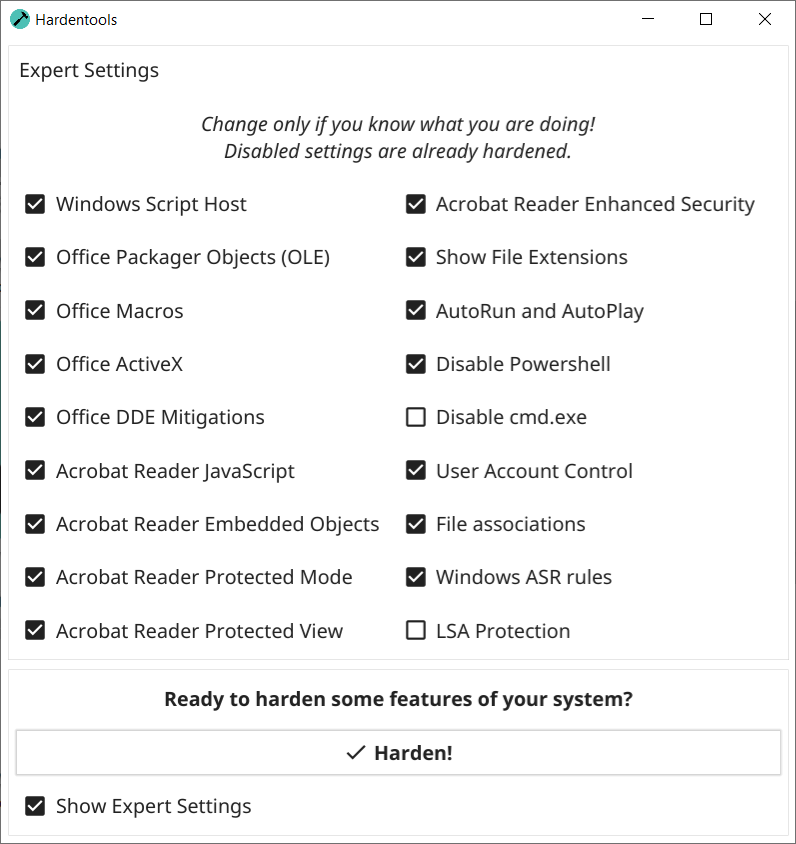
And that’s a quick and dirty solution, the quickest solution that you can have about hardening an endpoint. One thing to remember about this screenshot here is to be careful about disabling PowerShell, because if you disable it and you need it, especially on your own workstation, then well you’ll have to re-enable it.
For system hardening, Hardentools is the quickest and most useful tool you can use to secure an endpoint because it protects from various vectors of attack, such as Office files, Adobe PDF files, scripts, etc.
It is incredible how Adobe Reader can have new vulnerabilities every week for years and years, it’s just mind-boggling. Showing file extensions is critical because hackers send binaries
disguised as documents, with PDF icons, or Word document icons, and users usually open them without knowing they are opening a binary. If the file extension is showing, the user can at least see it’s a .vbs or .exe file.
Some people are “MCDC” – Microsoft Certified Double Clickers, they will just click and open anything they receive over email or IM, regardless of how many security awareness trainings you show
them, they will keep clicking on everything that hackers send them. You can’t prevent that.
You have to remember, that people will open stuff and you have to harden your endpoints against user error.
We need to go deeper!
The tool above is for really small organizations. You can use it on your home computer, you can use that tool for your child’s school PC or your parents’ computers. It is great for small companies without a centrally managed directory and endpoint security management systems.
Now, I’m going to show you a security hardening script that I’ve built by stepping on the shoulders of giants!
Of course, I used existing scripts out there and I made several hundred changes to the script before I could see it as usable for Production systems and before I could call it my own.
I want to show you what your defenses against ransomware should be, compared to a product you can buy.
First, it creates a System restore point.
Something to keep in mind: the script is 955 lines and it’s extensive, it has hundreds of security settings, dozens of settings just for Windows Defender.
Instead of going line by line in this article, the idea is to point out the ideas within the script and what needs hardening on your average endpoint/computer.
The objective is, even if the attacker managed to infect one machine, they would not be able to move across the network from machine to machine and propagate their access via various means. Most of these means are disabled by the script.
There are lines in the script which are commented out – that does not mean they should be ignored. One of them disables the installation of services remotely and kills the ability to run psexec remotely – and is extremely valuable. So read the script instead of running it blindly.
It’s important that you associate all kinds of executable content with Notepad so people who double click on everything wouldn’t infect themselves. When they still double click on everything, because they’re just a regular user, they will open the file in notepad and it will not execute.
This is critical, associating .bat files, javascript files, visual basic files all kinds of such files used by hackers all the time, such as .iso, because it mounts in a folder and mounts a read-only filesystem which your antivirus can’t clean or disinfect.
That should definitely not be allowed in your network, at least not for regular users.
Why do we recommend Windows Defender over the other antivirus vendors out there?
Microsoft has the benefit of more than a billion workstations running their operating system – Windows 10 and Windows 11.
With that amount of computers running their OS, they are able to collect real-time data on attacks happening globally, instantly. No other security vendor and no other antivirus vendor has that much data and that much threat intelligence.
Besides that, Defender has a ton of settings available only through deep system configuration, registry settings, and policy settings, not visible in the User interface. That is what this script which I show in the video, configures – a ton of Defender settings, making use of all these functionalities.
Killing the Microsoft Office or Office 365 attack vector
The script also takes care of a dozen settings relevant to Office documents and ways hackers may utilize them in their attacks. After running the script, these attacks are severely limited.
As you can see, hardening a workstation is not just hardening the operating system, you have to harden the operating system itself, you have to harden the Office suite, you have to harden the Adobe reader, you have to harden your Defender and all kinds of deep system components and settings.
The ways to compromise a machine are numerous, hundreds, and so the ways to mitigate these attacks are numerous, too.
Some of the settings in the script kill the ability of hacking tools to operate properly, too. One such tool is used in the initial stages of an attack, and is called “mimikatz”.
One thing that I would like to emphasize is the configuration of the local system firewall to block specific outbound traffic from specific binaries which are part of the operating system. By default, the local firewall allows any and all traffic originating on your machine towards the Internet. There are, however, programs regularly used by hackers and which are almost never used by regular users. These programs should never be allowed to communicate externally and so this script takes care of that.
Hardening your Browsers
The script you see in the video above also hardens Edge and Chrome, taking care of critically important things, such as blacklisting the javascript:// option in the address bar, installing an adblocking extension that also blocks malicious URLs, etc.
Browser hardening is critical for your defense from initial infection on the patient zero workstation because it is one of the main infection vectors for most cyber attacks. The other main infection vector is file attachments – and we already took care of that with our Office suite hardening section in our Windows hardening script.
What happens after the initial compromise of a user’s computer
Let us presume the user opened a malicious XLS file containing macros and got themselves infected. The hacker gains remote execution on the device and works remotely on it, as if it was your IT support department.
The next thing they are going to attempt is to persist their access.
And then, they will run hacking tools, such as mimikatz, or one of its dozen flavors – there is even one called ‘mimidogz’. There are powershell versions of it, javascript versions of it, etc.
If you have not hardened your machine, that tool will reveal your password and/or hash, in clear text. The Active Directory password and/or hash, or the local ones.
The user can then use these to log in to all other computers and servers where the hash would work. If your Domain Admin has logged in to a compromised machine ever before and their password has not been changed, it’s game over for your entire organization.
Why you should never trust your antivirus
Antivirus programs can be easily bypassed by even novice hackers, using tools that obfuscate and encrypt the malware so it would become undetectable. More advanced hackers can pretty much guarantee their malware will not be picked up by your antivirus.
If you do not harden your computer, it will be at the mercy of anyone who can make any malware undetectable by your antivirus. That includes even kids who can google stuff online.
That’s all I had to say for today I hope you liked this webinar.
Someone is asking about ransomware remediation steps. Well, I will answer that:
Ransomware remediation is not what you should be looking at.
You should be looking at the security breach that happened months before the ransomware! The fact is, there are hackers in your network and they have been there for quite a while. You should kick them out in a secure way, which is not easy. There are books on incident response, such as this one:

You should learn about incident response and digital forensics in order to kick hackers out of your network.
It’s a profession, it’s a job, not an article you can read or a webinar you visit in order to know how to do that job. You should have incident responders in your network and digital forensic experts on your team in order to know how to kick out attackers from your network.



