I really hate the word phishing!
Some genius security expert came up with it years ago and now the whole world has to explain it to users, as if they cared or as if it made any difference.
Now and further in this article, I will use the proper ‘fake zoom invitation’, ‘fake login form’ – which make sense. Nevertheless, if you are looking for phishing message or email examples, below are some samples you could use in your awareness campaigns:
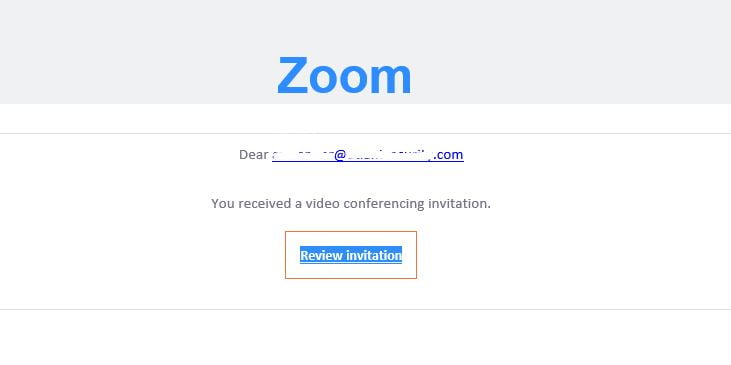
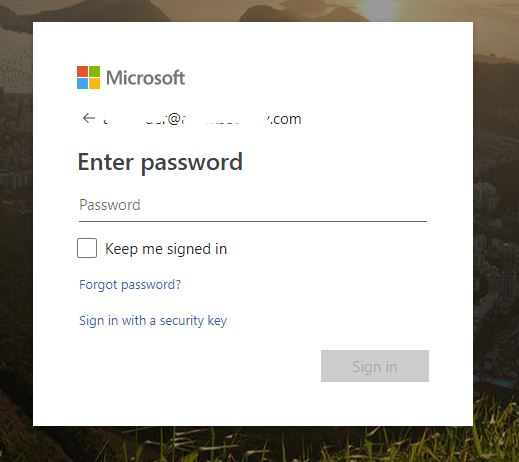
A fake Zoom invitation, which when followed, leads to a fake Microsoft 365 login form, which is the final aim of the hackers:
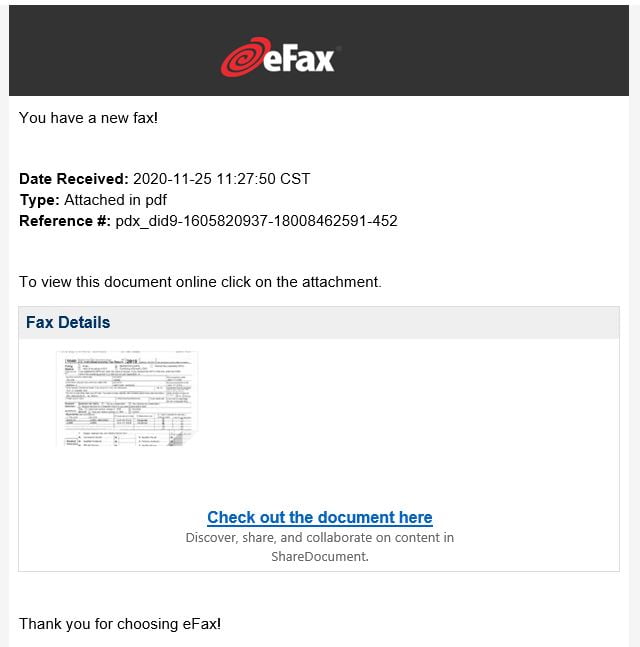
Hackers also love sending fake faxes to lure users into clicking on them and then submitting their login credentials (hey, nobody banned creativity, right?):
There is a very obvious sign for ALL fraudulent emails like these: they all ask the user to perform an action in order to see the alleged content, invite, fax, document.
Their logic is always the same: send a fake message which asks the user to perform an action (click, login, allow macros) to view the content.
Legitimate messages would just send the fax or just show the invite to Zoom.
Sometimes they claim that your mailbox is full or that you have pending unreleased messages somewhere:
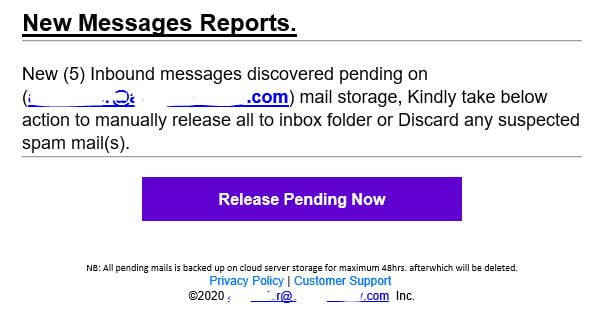
As I explained above, the logic is the same: click (do an action) to reveal content.



