We can help you fill the security questionnaires you receive from your clients. Here is a short video to summarize and augment this article:
Filling the security questionnaire adequately will help you win your client’s business or comply with their requirements to continue working with them.
Need help filling your security questionnaire? Schedule a free video call with us!
The article will require you to do a lot of work – but the results will be worth it.
If you read just one sentence on this page, let it be this:
Gather all stakeholders who might have the slightest idea about any question in the questionnaire and send them the file, to each of them, one by one, in sequence. Let them leave their comments on each question that is relevant to them. In the end, you can combine the comments into a relatively good answer for each commented question. For the rest, you have this article!
Sometimes the document may be named “Supplier onboarding checklist,” or “EDRM Security Audit Questionnaire”, but its purpose remains the same – to assess your readiness to handle cybersecurity risks.
If you need to know how to fill such a questionnaire, which sometimes can contain up to 290 questions, you have come to the right place.
Before you begin, there are a few things you should know:
- Every answer you give makes you legally liable for non-compliance in the event of a breach
- Many questions will sound alien, and your team will have no idea what they are about – do your research before answering
- Answering some questions with a “yes” will require you to go through complex and sometimes expensive projects. Make sure you communicate with your client about these questions – perhaps they are not critical to them in your specific case.
- Cybersecurity may be a completely new field for your entire team. Answering “compliant” may require people to change the way they do their job. Expect resistance. We can help you deal with the opposition in a smooth, productive way.
For smaller vendors, it is an impossible task to fill such a questionnaire by themselves. Each time they do, the result may sound logical to them but completely discredits them in their client’s eyes, who has a well-trained and experienced security team and can quickly spot when you pull answers out of thin air.
We helped our more prominent (8000+ employees) clients create similar questionnaires and vendor assessment processes to evaluate their partners and vendors. We know what they are looking for in your answers!
If you read this article carefully and follow it, you will have no problem filling the security risk assessment checklist you have just received.
Smaller vendors often fail to see the potential of diligently filling the questionnaire. They see such questionnaires as a bore, a bureaucratic obstacle that slows down their business and is annoying to their IT department.
What if you transformed your company and its IT operations to be secure? What if you ensured you stored and processed client data safely?
And we are not talking about “secure according to ISO 27001” or other auditing standards – we are using the word “secure” in the context of practical, actual security. Where you would go beyond a simple checkbox approach “We have 2-factor authentication” to “The 2-factor authentication we use is user-friendly and difficult to bypass, that is why we feel it is a good and secure approach”.
Here is a video that discusses 2fa bypasses in detail:
If you watch the video, you will understand where is the limitation of security checklists. They ask you the basics. “Do you have 2fa?”. Our recommendation to you, when researching how to fill a security questionnaire, is to dig deeper and answer them with greater detail.
Why?
Because by digging deeper, as in the 2FA example above, if you go beyond the basics, you will impress the client. Imagine their satisfaction if you fill the questionnaire with “We have a bypass-resistant 2FA method” instead of just “Yes.”
Impressing your potential client usually means winning their business.
If you fill the first one correctly, you will always fill similar questionnaires and checklists in the way your clients expect; you would instantly rise above your competition.
You will win business that 99% of your competitors will not, simply because they see such checklists as bureaucracy and a waste of time.
Be the exception, become secure, build your information security program, and you will always have the perfect answer to any client’s cybersecurity questions.
How to review the checklist or questionnaire before you start working on it
When you open the Excel spreadsheet or the online questionnaire, you will be presented with an overview and instructions on how to provide your answers.
Usually, it looks like this:
![]()
Or like this:
In Excel files, the instructions are usually in the first or second sheet. In online systems, you can usually find instructions for each section or particular question.
Sometimes, they may even include a diagram like the one below:
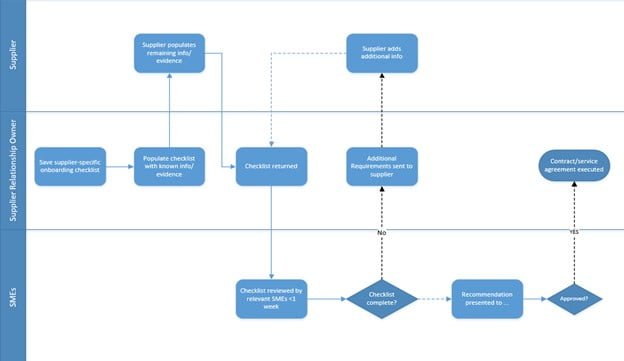
Spend enough time to understand the instructions, and do not start filling in the file until you are sure you know how to do it. If you have questions, now is a good time to refer them to the person or company who sent you the file.
Some questions are more important than others. For example:
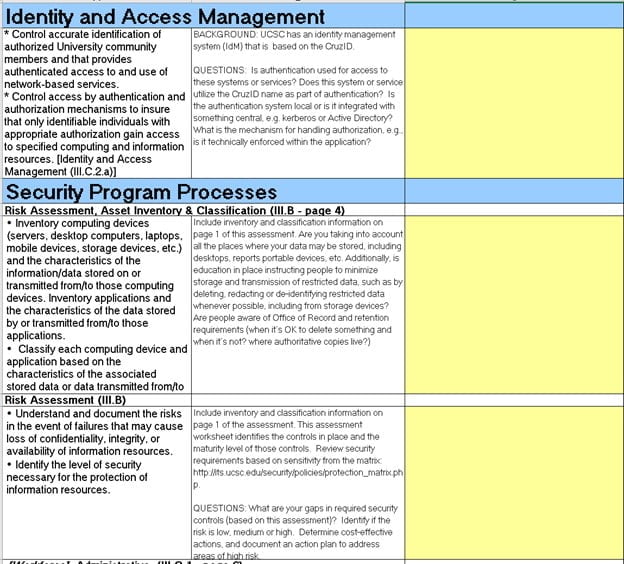
In this case, you see that Identity and Access Management is placed first, and the file asks you a generic question about your authentication and access management. This topic is the cornerstone of every security program, and you do not know how to answer this, which means you have very few controls in place and represent a significant risk as a vendor to your client.
Instead of trying to fix the answer and come up with something believable, we suggest that you try and implement an actual Identity and Access Management program in your company. It will serve you first and, as a result, provide value to your clients.
You can use the questions in such a questionnaire as a free security audit! Take advantage of not paying for the audit and do your research on what you should do and implement risk mitigation controls to impress your clients every time they send you such questionnaires and checklists.
Here is one more example of a vendor security questionnaire that we helped some of our clients become compliant with and then fill appropriately:
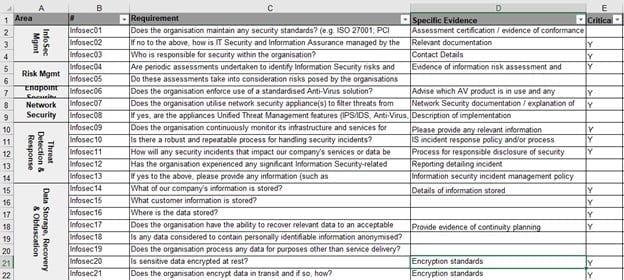
Many of these questions have a deeper meaning – usually, your client wants to see your answer and the processes and procedures along with the answer. “Yes, we encrypt our data” is much less valuable than “Yes, we encrypt our disks with BitLocker/AES 256, and we encrypt our traffic by encapsulating it in TLS 1.2 which is the minimum acceptable level of encryption according to our policies and procedures”.
How to answer 3rd party vendor security risk assessment questionnaires
Should you answer that question with “No”?
Answering “No” is more straightforward but can lead to misunderstanding on your client’s side.
Imagine being in their shoes, reading the filled security questionnaire, and seeing “no” everywhere.
Now compare that with the situation where you ask for clarifications about the criticality of missing the control or even ask their advice on prioritizing specific security control implementation to answer critical questions positively.
“Do you have a Data Leakage Protection?” might be the question. You may answer “No” to that.
But you may also ask, “Considering the ease with which DLP systems can be bypassed and the fact that we use this and that compensating control, can we mark this question’s answer as “Not Applicable” in our situation?”.
Hopefully, you see the difference between the two approaches.
Remember, you are not the last link in the chain. You got this questionnaire file because your client must comply with security rules and regulations and maintain a list of security vendors.
They cannot demand ultimate and perfect security from their vendors because even your client is not 100% secure. They know that.
Instead of simply answering “no,” use any or a combination of the strategies above.
Mark the questions you believe would be relevant for such an approach as “need clarification,” ask them which questions you should focus on, and ask them which security controls are a deal-breaker if missing.
Then focus on implementing these security controls, and then you will be able to answer positively in the questionnaire. Just like that, all sides have what they need, and everyone is happy!
Sometimes you might have budget constraints – and your clients will understand that, especially if you show them the compensating controls you have implemented.
How to fill the EDRM Security Audit Questionnaire
When we helped a client fill the EDRM security audit questionnaire, we stumbled upon their half-helpful “how to use” spreadsheet section. The help section is helpful only in terms of technicalities such as ranking calculation and mentions that if your company is compliant with ISO 27001, PCA, NIST, CIS – that you don’t need to fill anything further. And that is the extent of the documents’ help section.
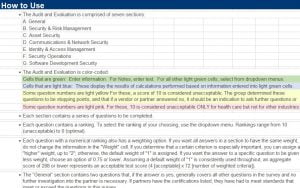
When searching their website for additional instructions you will stumble into an endless loop of blog posts and broken links.
Yet many companies continue sending out the EDRM security questionnaire and their vendors struggle to fill it correctly.
- Be very careful when selecting the ranking number for each question. The instructions are unclear as to how to determine is it 0 (perfect) or 10 (unacceptable). Here is how to determine the right number:
- If you believe the overall situation in your company regarding this question is adequate, you could select 1. If you are absolutely certain you comply with all technical, practical, policy, and procedure requirements for this question – select 0. For any discrepancy, up to ‘we are in trouble as we don’t even know what that means”, you can select up to 10, where 10 is the absolute worst – zero compliance of your company with the security controls required in this question.
- It is okay to select low ranking for questions that are irrelevant to you and you are not compliant with them. For example, if you do not store any health records and are not required to comply with HIPAA, you could safely select 6 or even 8. Do not select 10 – as 10 means “unacceptable”. If you are not required to comply with HIPAA, not complying with it is acceptable.
All sheets in the spreadsheet you received, except “Overview”, “How to Use”, “A-General”, and “Summary”, contain questions marked with yellow or red. Those are the really important ones which you should pay special attention to.
For example, the “Sec and Risk Mgmt” sheet contains question number 6, “For any data stored on your system that contains HIPAA information, Protected Health Information (PHI), Personally Identifiable Information (PII), or Payment Card Industry (PCI) information, will it be maintained in a properly protected environment? (encryption, monitoring, role-based restricted access, etc.) as required by regulations? Describe all standards and systems currently in place to provide protected environments.”
It is a mouthful, I agree!
And there are many such questions in this questionnaire.
Just breathe and slowly process the question. Essentially, it is asking you if you *should* comply with specific regulations and if you should, are you storing the respective types of data, and are you properly protecting it.
We highly recommend that after ranking and scoring the question, you carefully prepare your “Notes” section and do not leave it blank.
You should be detailed and specific as to which types of data you store and process and how you protect them. You can refer to other questions in the questionnaire where you have answered this part.
Types of security assessment questionnaires
- Consensus Assessments Initiative Questionnaire (CAIQ) Lite – often sent to vendors on the Whistic platform
- Secure Software Development questionnaire
- DevSecOps questionnaire
- NIST 800-53 v4 questionnaire
- NIST 800-53 v5 questionnaire



