Password, Identity & Access Management
We help companies secure their Identity and Access management practices in the Virtual CISO Services solution. We help companies identify all business assets, applications, infrastructure elements, data, and people with regular or administrative access. We also identify potential ways to attack or misuse the access and develop compensating controls for all risks identified.
A critical part of this project is to educate the customer’s whole team on the importance of not reusing passwords and how to use a password manager efficiently.
A vital objective to achieve with any customer is reaching passwordless authentication – something we deliver with a combination of services from Google (FIDO2), Microsoft (passwordless authentication), and Yubico, and utilizing biometrics and physical security.
Attack Mitigation
Every company has a different threat landscape due to its data, customers and competitors, and resources.
Because of that, hackers can use different attack methods to compromise the company’s security and achieve its objectives.
They could be after stealing money directly from the accounting department, stealing confidential data, or even holding the company for ransom, as happened with a famous law firm security breach.
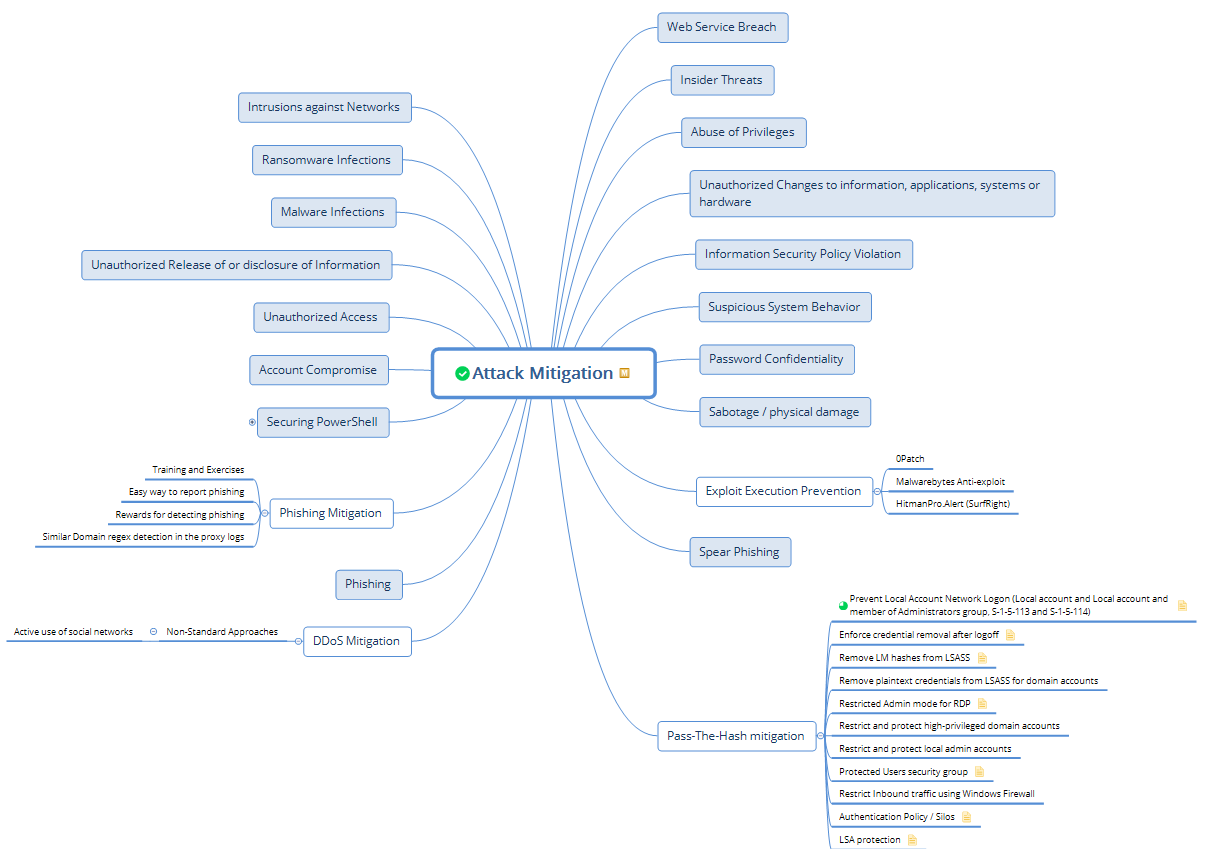
We take a lot into account, but we also cover the fundamental types of attacks with all our customers:
- Intrusions against networks
- Ransomware infections
- Malware infections
- Unauthorized release or disclosure of information
- Unauthorized access
- Account compromise
- Abuse of privileges
- Unauthorized changes of information, applications, systems, or hardware
- Information security policy violation
- Suspicious system behavior
- Password confidentiality breach
- Sabotage / physical damage
- 0-day exploitation
- Phishing attacks
- Spear Phishing attacks
- Web service breach
- Insider threats
We develop compensating controls for all of the above and implement them for our customers, depending on business priority and risk.
Cybersecurity Awareness Training
Customers who use our CISO as a Service offering receive regular, high-quality security awareness training, which helps every employee detect suspicious emails and report them.
The training is delivered periodically; we help the customer’s team track its completion. Besides the regular exercise, customers receive frequent updates on new attack methods that hackers use globally, keeping their team alert and up-to-date.
The human element in every defense strategy could be the weakest link or your most reliable link – it all depends on how well people prepare before they encounter an attack.
Cloud Security Architecture
Are you using any major cloud providers – Google, Azure/Microsoft 365, or Amazon Web Services?
We develop secure architecture guidelines and help our customers implement them regardless of which cloud provider they use, even a small, regional one. The mindmap Atlant Security created is the foundation of the elements to be protected in any cloud deployment.
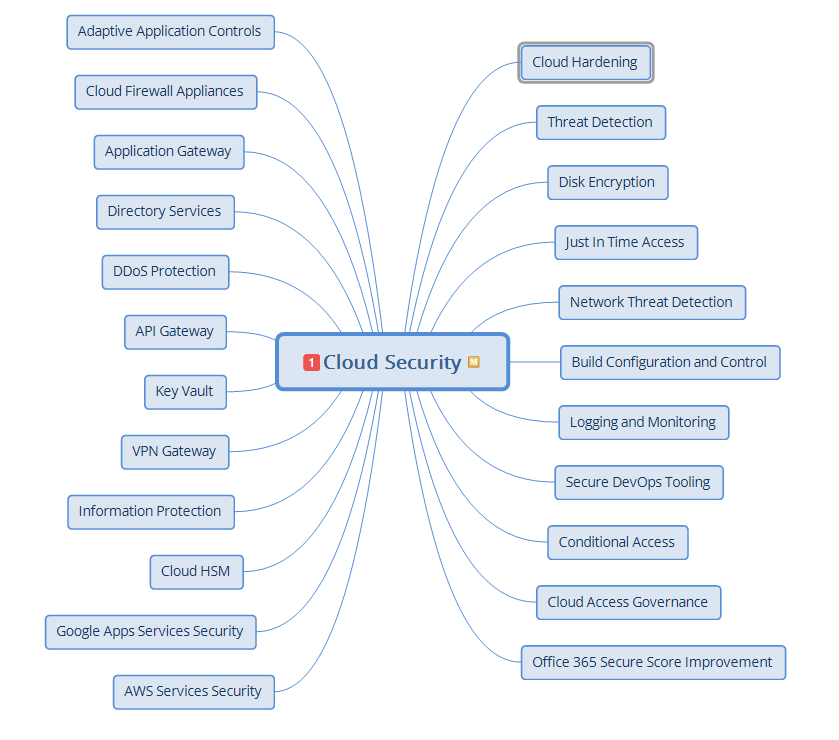
We also offer cloud security consulting as a separate service – so check it out if you want to start with cloud security only. However, it is more effective to get everything in one package.
Cloud Virtual CISO
Some business cases require that a company hires a virtual CISO service for its cloud-only environment. We already have several clients matching that description – with a 100% cloud-based IT infrastructure; some even host their desktops in Amazon Workspaces.
If you decide to migrate to the Cloud, the skills of a regular CISO are no match for your needs, and it is understandable why you may have trouble finding the right skills in defending cloud environments. Let us help you; our team has all the experience you need!
What does it take to secure your IT infrastructure?
Here’s a surprise: your printer can be the most accessible entry point into your network! Just check this PDF from BlackHat: modern printers have an operating system and often contain administrative credentials.
But there is more to security than securing printers!
Windows 10 has 282 security settings, of which 25 are critical. The situation is the same with Windows Server, Exchange, Mac OS, network devices, firewalls, and switches. We take pride in our enterprise system hardening procedures and don’t stop there.
The diagram below shows our process when securing our clients:
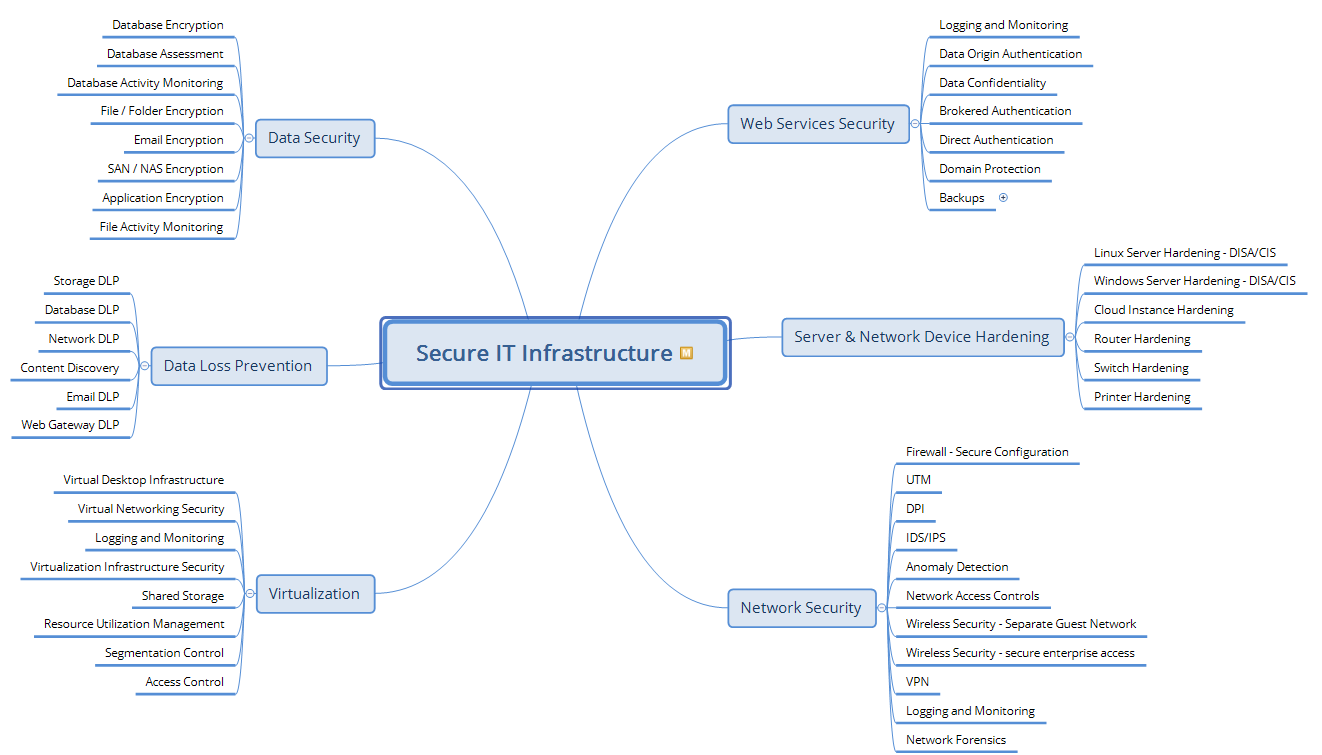
Very few CISOs go to the length and depth of our Virtual CISO Service offering. Our part-time CISO service is not cheaper than a full-time Chief Information Security Officer’s salary – but it achieves at least three times more than if our customers hired someone full-time.
How vulnerable are the elements in your network, and do vulnerabilities decrease over time?
Every element in your network can and usually does have vulnerabilities. When clients sign up for our Virtual CISO services, we help them create and manage an efficient vulnerability management program.
Switches, routers, firewalls, servers, desktop computers with various operating systems, and all the installed software have new vulnerabilities posted for them every week.
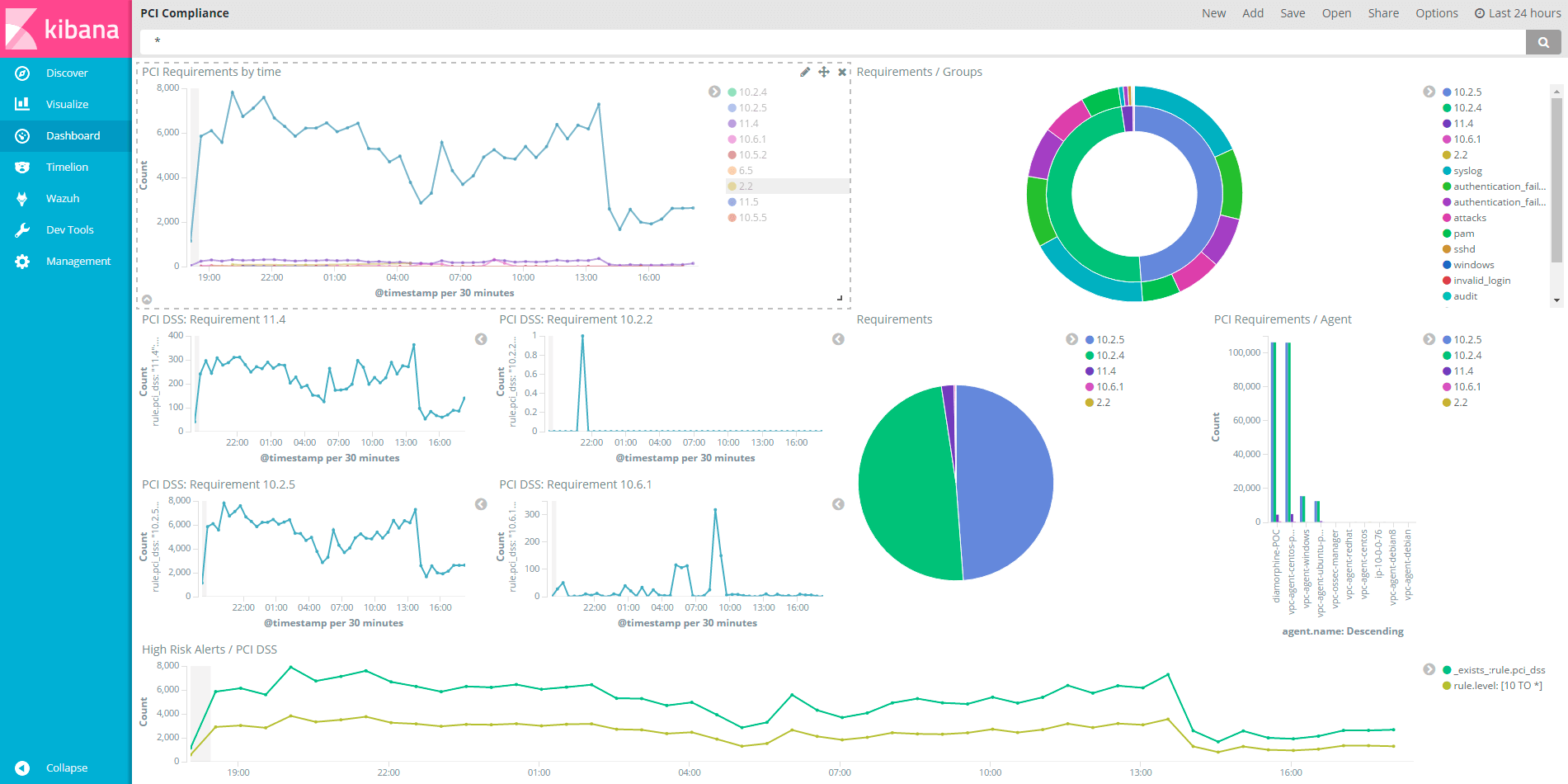
Do you maintain a record of the following:
- How many vulnerabilities do you have in your network on average per month
- Does that number decrease over time
- Do you improve the speed at which you patch vulnerabilities once they become known
- How often do you scan, and what do you do with the scan data once it discovers new vulnerabilities
- Do you improve your patching practice and your vulnerability management KPIs over time?
Securing email, collaboration, and instant messaging communications
Part of our Virtual CISO service is protecting email services on-premise and in the Cloud and safeguarding collaboration tools such as Trello, Jira, Microsoft Teams, Zoom, and our clients’ instant messaging services.
The reason they need to be protected is simple: hacking them is easy. It can take less than 2 minutes if you have not tried to secure them!
By taking the role of a CISO for your company, we constantly monitor all your email accounts and services for signs of unauthorized access. Even with 2-factor authentication enabled, breaches could still be possible, and that is why it is critically important to integrate proper security monitoring with any security control.
When should you perform Attack Simulation / Penetration Testing?
Penetration testing is essential in every Information Security Program and part of our Virtual CISO as a Service offering.
However, penetration testing often lacks strategic planning or a comprehensive Information Security Assessment. Executing a penetration test after completing the significant efforts to build your Information Security Program is crucial.
If attack simulation is the first stage of a company’s security efforts, the penetration test results will only show the lack of security controls. In that case, it will completely waste time and resources.
Why is Secure Software Development part of our Virtual CISO as a Service offering?
Secure Software Development is more than following an industry best practice or guideline.
It is about culture.
The culture of enterprise architects designing secure solutions; Development leads requiring specific standards of secure coding from their developers;
QA testers know which security vulnerabilities to look for – logical and technical; the IT administrators build secure development, testing, and deployment environments for everyone working on the product;
Security testing is when the product has to be declared safe and secure by its clients and users.
We help startups and software development companies build and nurture this culture.
Policies and Procedures are a company’s Constitution
Our Virtual CISOs, as Service experts, carefully examines every client’s business before working on their security policies and procedures.
Our Virtual CISO Services can create many policies and procedures for you. For example, we could create a “Security Hardening Procedure” for your IT department, which is not on the image below, or combine several policies into one. Still, it takes decades of expertise and experience to know which business processes need extra security in a policy or a procedure. It all depends on a customer’s business requirements and what makes sense.
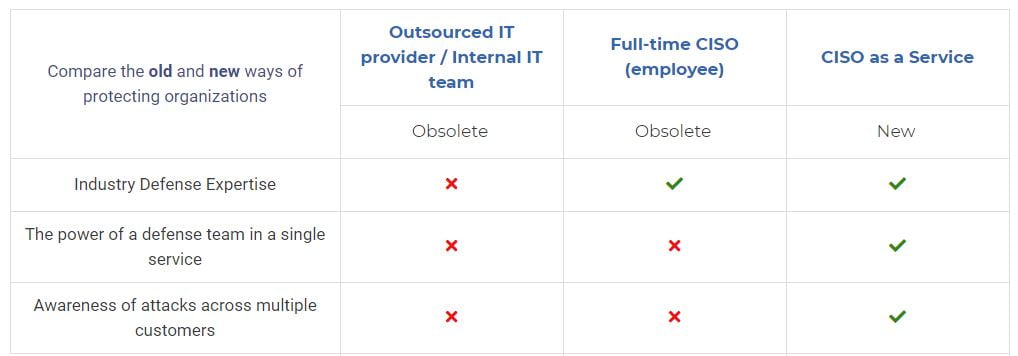
CISO-as-a-Service is gaining popularity among the $500m – $2b businesses.
Can a team of seasoned CISOs and security subject matter experts replace the CISO role at an organization by taking the Virtual CISO role?
In 2009 a CISO had to ensure they passed their annual audits and that their antivirus worked correctly. In 2019, a CISO must:
- Ensure patching is on time for all 9000 different applications, operating systems, firmware, and drivers in their environment
- For all the same 9000 elements, maintain daily/weekly/monthly vulnerability management.
- Maintain yearly penetration tests, and ensure the findings get fixed before the next one.
- Choose between many security vendors selling their Data Leakage Protection, Next-Gen Firewalls, Blockchain and AI-based antivirus, antispam, and anti-(insert snake oil salesman keyword here). They primarily sell just a fancy box with a fancy name that the hackers don’t even notice as they come in and take your data.
- Herd all your employees into security compliance
- Establish Security Incident Prevention, Detection, and Response
- Communicate risks to the board and get adequate funding for their mitigation
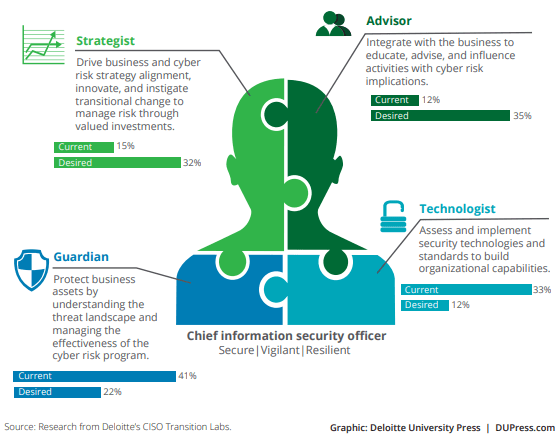 The likelihood of finding someone who can successfully contain all the knowledge and achieve your above performance objectives is incredibly low.
The likelihood of finding someone who can successfully contain all the knowledge and achieve your above performance objectives is incredibly low.
Our CISO As a Service team will build or rebuild your security program.
Protecting business-critical data needs to be aligned with business needs. On top of that, which elements would you like to have as part of your security program?
We help organizations improve processes like threat management and building an Identity Management Program. We also help them to establish prevention, Detection, and Response practices. And we even provide security awareness training for executives, regular employees, and IT departments (all of them need different content).
Traditional security program building takes too long. You must figure out the right path, tools, and techniques to jump ahead.
We have seen some old processes and technologies being used – and the people using them thought that just because it was in use for so long, it was still effective and relatively risk-free.
Instead of training your staff and growing your internal capabilities, now you can access a senior resource part-time, maybe a day a week or 4 hours a week, to speed things along.
Some organizations decide to buy things like security appliances and software – and within two years of going that path, they realize that the value of the stuff they bought is not what they expected. Sometimes your budget for a product but then realize you also need to find the right people to operate it or train them – and their compensation was not budgeted at all! That ends up considerably slowing the whole process down.
We can navigate that kind of minefield and ensure that everybody thinks of that kind of variable before making decisions and investing in a technology or solution.
What is the cost of a Virtual CISO Service?
The price for having our team be a company’s CISO depends on our security assessment results and the number of people and hours dedicated to defending your company. Our prices reflect that as all our clients are of different sizes and have additional security requirements. The price is slightly higher than what you would pay for a full-time CISO because you get more people, technology, know-how, experience, and a higher quality of service, which does not go on vacation nor could leave you for a higher-paying job. It starts at $40k per year for smaller companies, and for companies with thousands of employees, it may reach $300k per year or more, depending on any additional services and licenses a large company may need.
What is the average Virtual CISO hourly rate?
Get a Cloud Virtual CISO/CISO as a service instead of spending months searching for a good Information Security Manager. We bill clients annually or monthly because we essentially become a part of your team and deliver results on a project basis, targeting specific defense objectives. But since so many people ask us for the price, we can say that the price for smaller projects is higher and is around $200 an hour. For larger projects, where the work is distributed over a long time and involves much more billable hours, the price can be as low as $100/hour. Virtual CISO consulting services rates strongly depend on the project’s complexity.
CISO as a Service pricing
You can expect to invest between $5200 and $9000 if your business has only cloud infrastructure and you have between ten and a hundred employees. If you have a large IT team and your software development team is more significant than 20 people, then our CISO as a Service pricing will be higher than $10000 monthly.
The CISO as a service pricing starts at $5200 because a small company needs at least 20 hours a month and will most likely require at least 40 hours in the first month to get rid of all the high criticality risk vulnerabilities we usually find. You can expect the price to decrease after the third month because our involvement gets lower the more vulnerabilities we help you patch and the more secure you become.
Full-time CISO vs. a Virtual CISO
A dedicated full-time CISO usually spends one, two, or even three months understanding what is happening in a company.
It is essential to be non-disruptive by getting into processes you don’t yet understand, even if you are vigilant to raise the bar in defense of the organization quickly.
From there, one could determine the maturity level of an organization and build a strategy.
Differences and Similarities
The goals are identical, but there are some differences and similarities between a CISO and a virtual CISO.
Differences:
- As the virtual CISO provider, we don’t get to be at the company daily.
- We don’t have the time to sit back for 30, 60, or 90 days and learn the organization before acting and delivering value.
- There are certain expectations from leadership – we get paid for results rather than just being there for compliance.
- The project and control implementation speed is higher with a virtual CISO due to less incentive to procrastinate – we get paid for results.
Similarities:
- Our goal is to help the business run safely and efficiently.
- The resources needed to achieve a certain level of defense are very similar: you need to buy the same software and hardware.
How do we deliver the Virtual CISO service?
We might start with different projects depending on the organization’s maturity level. We usually begin with a NIST CSF (NIST Cybersecurity Framework) assessment and how it matches its requirements. We typically run our Cybersecurity Risk Assessment service, including NIST CSF elements, based on the NSA-ISAM (NSA Information Security Assessment Methodology). Sometimes we go deep and include breach susceptibility (penetration testing).
Using the results and the report, we establish a baseline for the client – in parallel to understanding the environment and culture at their company.
We also look at the deliverables the client sets in front of us (if any) and prioritize according to the business’s risk. We identify the major priorities for the first three months – the essential items on our list are usually the risks identified that present a direct threat to the organization.
After identifying those and working on them, we developed a 2 to 3-year strategy for the larger organizations and a one-year plan for the smaller ones, detailing everything we can tackle from a budget and resource perspective.
The limitations from the customer’s side are usually time, people, and resources available for security – and so with the results of our assessment, we strategically prioritize them with the client. We can often request more people and resources to cover the risks identified before materializing realistically.
What are the costs involved?
The first point we usually get into when people look at the virtual CISO option is cost – and from a pricing perspective, it is less expensive to have a virtual one. Sometimes you can’t even find a good one on the market! A CISO typically makes around $200 000 annually, and most organizations have not budgeted that amount for someone to take care of security.
Hiring and keeping the right talent is expensive and risky – many people leave within a year or two, and you would have to go through the same process repeatedly, which can take up to six months even with a good recruitment head-hunting team.
Let’s not forget that’s just the salary – excluding the price of any software, hardware, and external help they need to order – such as penetration testing, incident response, EDR, SIEM, and all kinds of other security services.
If you decide to get a dedicated CISO, you must get a headcount below them.
Let’s do the math, budgeting for a CISO position:
- The average CISO makes around $200 000 a year.
- The average security firm also needs to hire people to man the security tools in a company (especially those larger than 1000 people): someone has to maintain all those firewalls, SIEM (Security Information and Event Management), Antivirus engines, antispam, Data Leakage Prevention, exploit mitigation, Enterprise Detection, and Response tools (EDR), vulnerability management and patching tools… consider each of the new hires costing the company $50 000 – $80 000 per year.
- All the tools mentioned above have licensing costs, and the SIEM alone can cost $40 000 per year.
- Hardware and storage costs for all the data needed to be processed and stored for security purposes
You get to use our whole team of seasoned professionals under one service name: CISO as a Service with our service.
The cost savings are apparent. Let’s take recruitment, for example:
Any head-hunting company charges one or two monthly salaries for finding a CISO; the same applies to other people in the security department.
The average lifespan of a CISO in a company is 1-2 years (source: ISSA.ORG). That means that every 18 months, you will have to spend $20 000 – $40 000 on finding a new CISO and another $5000 – $8000 for each additional team member.
With our service, you save roughly $40 000 every 18 months just on recruitment costs, and you’re getting a higher quality of service. Add to that the cost of re-training every new hire, as they spend up to three months (paid!) learning about their new job and requirements.
On average, the longevity of a CISO in a company is around two years – because they can lose their job for all kinds of reasons, security incidents being just one kind. Yet another reason to go with a virtual CISO – you get to keep improving your security program with the same team, avoiding some of the political and interpersonal relationship risks present when tensions between CIO, CEO, and CISO arise.
For a security program to succeed, employees must stand behind the security strategy laid before them – including the IT and leadership teams. Everyone should care and participate equally, trying not to click on phishing links, reporting suspicious activities, trying not to bypass security measures, and instead writing when they are ineffective so the security team would find better usability and efficiency.
From a CISO service delivery perspective, our responsibility is to help everyone on board to stop seeing security as the ‘department of No’ but as a department that supports business and ensures its survival in the long run.
Our message is: “Here is our assessment of the situation, here are the risks, here are the potential remediation actions from a risk perspective – accept, mitigate, transfer, etc..”
Then the response method, based on the options provided, is with the client’s leadership team.
Who should the Virtual CISO report to?
In most cases, especially in organizations with a less mature security program, the CISO function reports to the CIO – and it might be the most effective form of reporting for them.
Being inside the team is often better than being outside the IT team and telling people what to do without directly seeing the impact of your suggestions on their projects.
If the networking team in the company also does security, when a CISO as a Service expert comes in, they may be viewed as a threat.
We must understand the personnel culture and tactfully diffuse things quickly to build trust.
Sometimes, after we start delivering our Virtual CISO services in the company, we still need to sell ourselves to the internal teams and team members – and we do.
Virtual CISO Responsibilities
The Information Security Program defines the responsibilities of a virtual CISO (or the company delivering the CISO as a Service offering) created for a customer. They may range from external consulting to hands-on implementation, assessments, team, and individual employee mentoring, security awareness training, hardening security audits, random spot checks, financial reporting on the money spent on cybersecurity to the board, and much more.
Industry Relationships
We have a vast network of friendships, acquaintances, vendors, and industry professionals. We consistently leverage that network to offer a more streamlined and cost-effective service.
On the other hand, when a CISO stays in the same position and company for a long time, its professional network becomes stale and offers less leverage over time.
One of the great benefits of working with our company is the talent we have – even if one is not a PCI expert, when our clients fall under PCI compliance, we can always bring in a phenomenal PCI expert from our team to help them.
Another point is sharing industry knowledge with other consulting companies – 99 percent of the time, we’ve got the same attackers and defend the same infrastructure types. We have about the same technology and we all desire to share success stories to help others mitigate similar threats.
At Atlant Security, we also share information internally in our daily meetings and internal chats – the speed of information flow is much faster than a CISO can afford to read during their daytime job activities.
Our primary responsibility is communicating risk to the business and providing the right tools and expertise to act accordingly.
Assistance with your migration to the Cloud
Almost everyone uses one or many cloud services – businesses even migrate all their infrastructure and data to the Cloud. The digital transformation movement is swift, and technologies change quickly – quicker than many full-time employees are comfortable with.
That is where our CISO as a Service comes in – to bridge the gap between the data and services you need to migrate and the internally available resources.
We always have the needed skills and personnel available, significantly speeding up your cloud migration and reducing friction and risk.
On Monday, we might be in an organization and work with their own set of business drivers and political obstacles to mature their security program.
On Tuesday, it could be a completely different organization, in a separate vertical with varying needs of business and requirements, and it is challenging. By overcoming various challenges, we add to the whole team’s experience – and all our customers benefit from that.
Can a company outsource all of its security needs to a third party?
It’s important to understand that you can’t do everything at once. You need to identify the number 1 priority which will bring the most impact quickly in improving the organization’s security.
No company can offer a complete set of managed security services unless the client generally outsources most of their processes – their whole IT organization – to a third party.
If there is on-site infrastructure, someone, even a member of the IT department, must do things as instructed by our virtual CISO team.
Is CISO as a Service the same as Part-time CISO?
Having a part-time CISO with our service is better than having a full-time CISO because you get guaranteed service levels and defenses. Hiring full-time means you pay one salary to the headhunter or recruiter/recruitment agency, and you need to train the person in the specifics of your company. That training period usually lasts a few weeks to a few months, depending on its side and the CISO skills.
Part-time CISOs need less time to commute if they work remotely, which gives them more time to work on the company’s defenses. With our service, you can get a highly experienced and qualified security expert to be your part-time CISO.
The team serving as your CISO is always motivated and consistently performs at their highest capacity due to the KPI-based contract between our clients and Atlant Security and the performance rewards system based on client satisfaction and goal achievement.
When you have a CISO-as-a-Service contract with us, it clearly defines the Key Performance Indicators (KPIs) and objectives. Our invoicing depends on the KPIs achieved, agreed and approved by you.
Imagine if you could approve the work of your full-time or part-time CISO before each salary. Unfortunately, no labor law in any country globally would allow that. But it will enable it with a service contract with a company! Their performance would have been excellent, too!

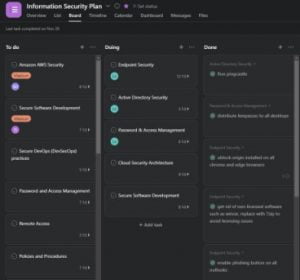 Once we start working together, we will generate a Kanban dashboard for you.
Once we start working together, we will generate a Kanban dashboard for you.



 The likelihood of finding someone who can successfully contain all the knowledge and achieve your above performance objectives is incredibly low.
The likelihood of finding someone who can successfully contain all the knowledge and achieve your above performance objectives is incredibly low.