Atlant Security © 2024. All rights reserved
Do you REALLY know WHERE your security weaknesses are?
Our customers are assessed using our unique Information Security Assessment methodology based on the NSA-ISAM, NIST 800-53, and the Baldrige Cybersecurity Excellence Builder by NIST – a unique combination you will not see anywhere else, globally.
At Atlant Security, we provide more than just an information security risk assessment for our clients. We will also provide consulting on every finding we discover so you know exactly how to remove the security risk from your company for good. This will include a detailed action plan with steps to follow and clear objectives that we will ensure you achieve so you stay clear of security breaches that can cost your business valuable time and money. This means we offer an all in one solution to your business so you don’t have to go and spend more money elsewhere.
Forget the boring reports. We develop a complete Information Security Program for you, with detailed steps to follow for your technical team. We have done this for banks and nuclear power plants in the past – it is your turn to go through our assessment!
People store passwords everywhere and reuse their online shopping password for their corporate email! To top it off, their password is P@ssword123 or its variation and is guessed in 5 minutes. We help discover all such practices.
We check for existing mitigation controls for 17 types of cyber attacks: account compromise, unauthorized access, ransomware, network intrusions, malware infections, sabotage, security policy violations, etc.
We will check what is the effectiveness of any existing security awareness efforts in the client's business.
We will also find all business areas where the employees are particularly vulnerable to social engineering attacks and in need of additional specialized training.
Microsoft 365 has 280+ security settings. Amazon Web Services and Azure have hundreds of security configuration options, too - we will discover and document all security improvement opportunities in your cloud infrastructure.
We help our customers discover weak security configuration in their IT infrastructure by checking Server & Network Device Hardening, Desktop Hardening, Network & Web Service security, Data Security, Backups, etc.
How many vulnerable machines / apps can a company have in its network?
How effective is your Vulnerability management program?
Can your email access be easily compromised and in which ways?
Can hackers access your instant messaging communications?
Can information be easily leaked via email?
3 questions:
1) Have you ever performed a penetration test?
2) Was it performed in the best way possible or did you do it just for compliance reasons?
3) Do you want to experience a proper penetration test?
Software development should be a rapid, secure and efficient process. Do you follow the right secure software development best practices and if not, which ones should be implemented urgently? Our security assessment will find out!
Policies and Procedures are the governing laws of a company's business. Are your in use? Are they effective? Do they hamper your business in any way? Let us find out!
Secure Work From Home is one aspect of remote access, but what about third party partners and outsourced employees, vendors and guests? Remote access to sensitive data is not limited to VPN.
And this is exactly why we expand your defenses beyond VPN and add Zero-Trust as your main principle of defense. Are you ready to move on to the next era of access control already used by Google, Microsoft and many others?
Antivirus is just one of 12 controls we look for to see how protected your endpoints are from advanced hacking attacks. These controls help prevent the exploitation of these devices via malicious documents, scripts, 0day vulnerabilities and more.
Can you detect an attacker in your network today? If not, how are you sure they are not in your network? We will test your security monitoring capabilities and suggest concrete actions to strengthen them.
Every Information Security Program we build and execute for our clients is different. Their teams, infrastructure, applications used and business objectives are differ and we often expand our services to serve them better.
The only way to map a customers’ security journey is to assess where they are and where they want to be in a year.
The output of the Information Security Assessment is a detailed report with deeply technical step-by-step recommendation, but the real value of the assessment is in the Information Security Program Plan you will receive.
Our Identity and Access management service It is part of the CISO as a Service and is an ongoing effort throughout the entire time we work with our customer. During that time, we identify all business information assets and all people having regular or administrative access to them. We also identify potential ways to attack or misuse the access and come up with compensating controls for them.
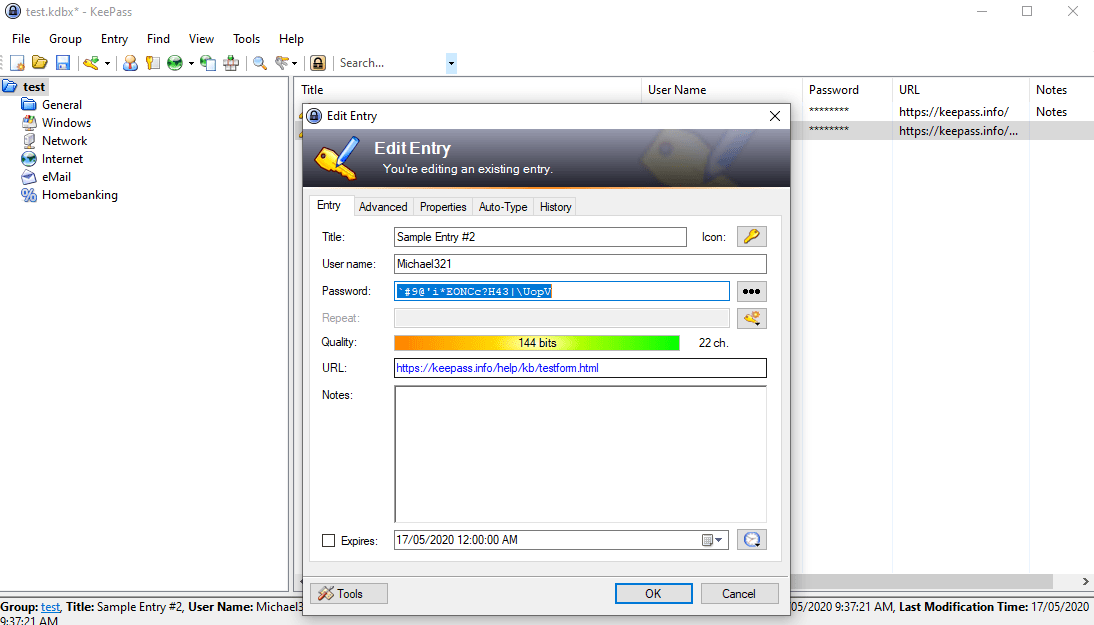
A critical part of this project is to educate the whole team of the customer on the importance of not reusing passwords and how to use a password manager efficiently.
An important objective to achieve with any customer is reaching passwordless authentication – something we achieve with a combination of services from Google (FIDO2), Microsoft (passwordless authentication), Yubico and utilizing biometrics and physical security.
Every company has a different threat landscape due to the data it holds, its customers and competitors and the resources it operates with.
Due to this, there are different attack methods hackers can use to compromise the security of the company and achieve their objective – to steal money directly from the accounting department, to steal confidential data or even hold the company for ransom, as it happened with this famous law firm security breach.
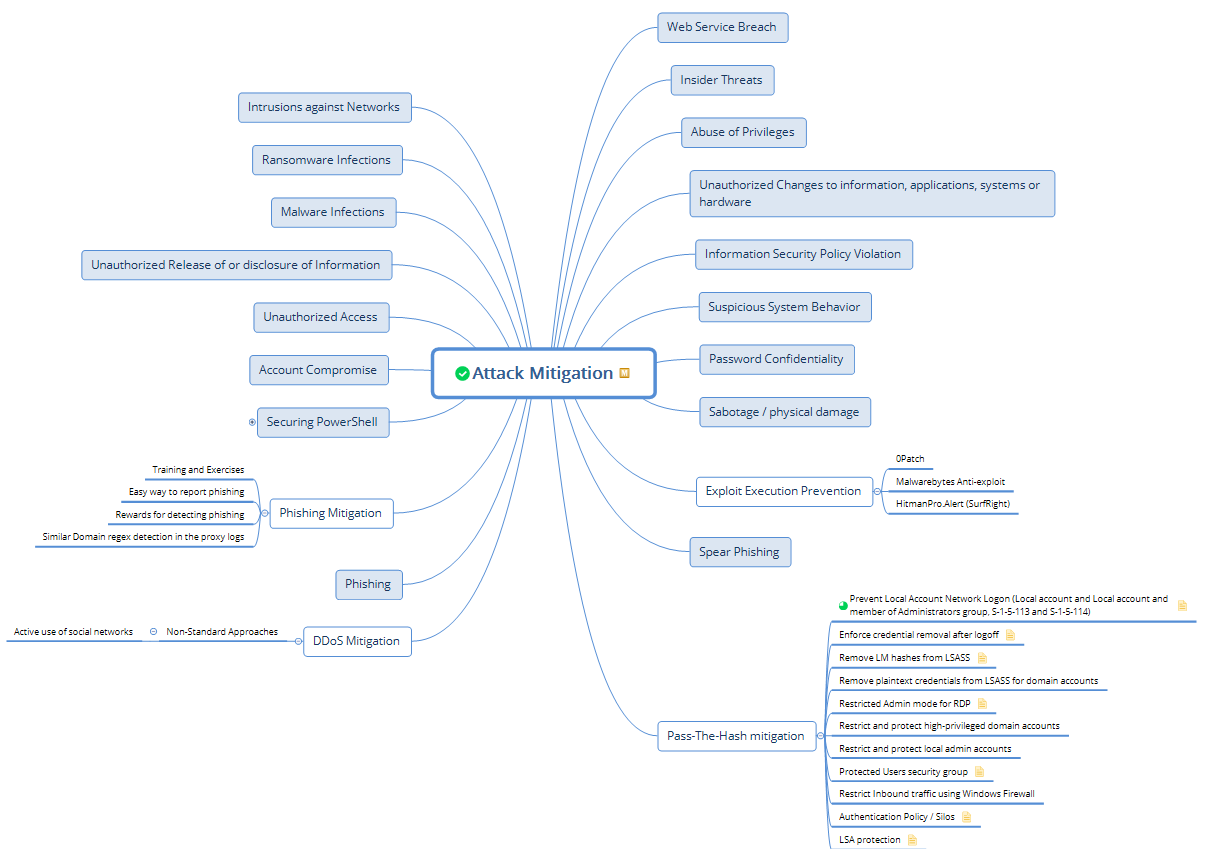
We take all of this into account, but we also cover the fundamental types of attacks with all our customers when conducting a information security risk assessment.
We come up with compensating controls for all of the above and implement them for our customers depending on business priority and risk.

Atlant Security © 2024. All rights reserved