Top Cybersecurity Consultant Companies: Choosing the Right Partner for Your Needs
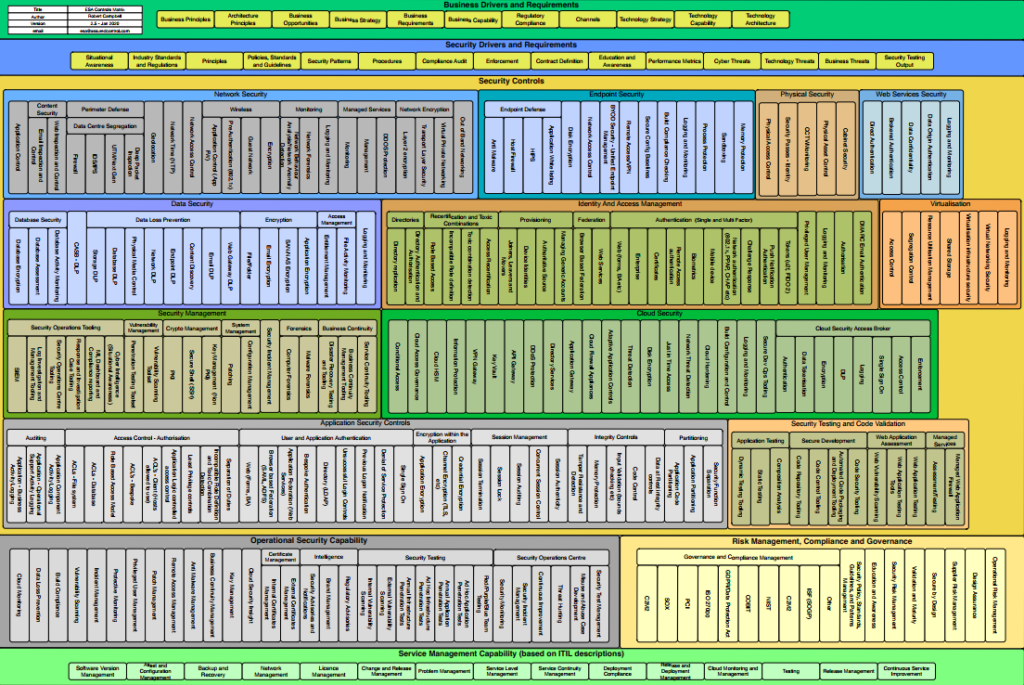
We will cover much more than just a list of cybersecurity consultant companies. How could that work out in your favor if you didn’t know how to select one? Hacking teams use complex sets of techniques, which cannot be defeated by simply getting a bunch of security products from a reseller: This is why working […]
2024 Cloud Security Best Practices: Securing Your Business in the Cloud
The year 2024 continues to witness a surge in cloud adoption as businesses across all industries seek to benefit from the operational efficiency, scalability, and cost savings afforded by cloud technologies. As the transition to cloud environments accelerates, so too does the need for robust security measures to protect sensitive data, systems, and services within […]
Fighting Cyber Threats in the Shadows: The Importance of Continuous Dark Web Monitoring

As we enter 2024, the dark web has become an ever-present menace, harboring a sinister marketplace for illegal transactions, from stolen credentials and personal information to malware and cyber attack services. The expansion of this underground ecosystem has led to increased risks for businesses of all sizes, regardless of industry or location. As cyber criminals […]
Ensuring Cloud Security: Essential Components of an Effective Cloud Security Audit

The widespread adoption of cloud computing has revolutionized the way organizations manage and store their data, offering numerous benefits such as scalability, cost savings, and efficient resource allocation. However, the shift to cloud-based environments also introduces a new set of security challenges, making it crucial for organizations to reevaluate and adapt their security audit practices […]
Empower Your Team: User Security Awareness Best Practices for a Stronger Cybersecurity Culture

In today’s rapidly evolving digital landscape, cybersecurity threats persistently target businesses of all sizes and industries. As we navigate 2024, one of the most effective ways to mitigate these risks is by fostering a robust cybersecurity culture within your organization centered on user security awareness. With the majority of cybersecurity incidents originating from human error, […]
Strengthening Supply Chain Security with Comprehensive IT Security Audits

In today’s interconnected global economy, a robust supply chain is vital to the success and stability of businesses across various industries. However, ensuring supply chain security has become an increasingly complex challenge as organizations navigate a myriad of potential threats and vulnerabilities. A single security breach or disruption within the supply chain can have devastating […]
Maximize IT Security Audit Value: Expert Tips from Atlant Security Professionals

Undoubtedly, IT security audits play an essential role in protecting your organization from cyber threats. However, to make the most of these audits, it’s crucial to approach them with the right mindset and strategy. In this article, we will provide you with valuable insider tips from Atlant Security’s experienced professionals, helping your organization maximize the […]
Strengthening Your Cloud Security Posture Through Comprehensive IT Security Audits

As more organizations embrace cloud-based services to increase efficiency, scalability, and agility, the importance of maintaining a strong cloud security posture becomes paramount. While the cloud offers numerous benefits and opportunities for businesses, these advantages come with inherent security challenges that must be properly addressed to fully realize the potential of cloud-based operations. Neglecting to […]
Uncover the Truth About IT Security Audits with Atlant Security’s Expertise

The world of IT security audits can be confusing and intimidating, with many myths and misconceptions influencing organizations’ decisions and perceptions about this essential process. The truth is, conducting regular IT security audits is vital for maintaining a strong cybersecurity posture and ensuring regulatory compliance. Demystifying these misconceptions is crucial to making informed decisions and […]
Implementing a Remote Work Security Strategy Through IT Security Audits

The widespread adoption of remote work has been a significant development in the modern workplace, accelerated by the global pandemic and the rapidly evolving technology landscape. While remote work environments offer numerous benefits, including increased flexibility and reduced operational costs, they also present unique security challenges that organizations need to address. The shift to remote […]
