What is phishing?
A fake web page, collecting credit card details from gullible users? Or a badly written e-mail asking you for your banking username and password? Or is it someone asking you to fill a survey, where some of the questions quietly ask you for your corporate username and password?
Is it the act of sending of the fake link, message, e-mail, or is there more to it than most of us perceive?

Lots of questions to answer.
Let me start from a different angle. Let us look at phishing as a bank heist.
A bank heist starts 3 to 12 months before the actual event – when a few criminal minds combine with the idea to rob a bank. Then they choose their target based on research – which one has the weakest security, which one has the best routes of escape, which one has the most money accessible with the least effort, etc. They establish monitoring of the bank 24 by 7 for several months, they monitor the lives of every person of interest, they go through their trash, read their mail, follow them to and from work, they know when the security guards change shifts, when the money arrive and leave, they know how well protected are the money and when are they the least protected.
At the end of this extensive research the criminal group knows the security of their lucky bank better than its CEO. And if they did their work well, the bank heist will be successful. But think about it… can any criminal group rob a 100 banks at the same time? http://www.ibtimes.com/hackers-steal-1-billion-biggest-bank-heist-history-could-they-take-down-whole-system-1818010 – yes they can.
This was not possible just a few years ago, but it is possible today.
Enter the age of Cyber Crime. And here is where we link phishing to the bank robbery above – because you don’t need to rob a bank physically, and phishing is how it happened for all of them. Because it is the final stroke of a criminal mastermind, the final step in a long journey to obtaining access to your company, in most cases.
Yes, phishing is THAT SERIOUS.
And it is time to answer the questions asked before. Is phishing just a fake web page? Well, think about the criminal group I described earlier. Is the man drinking coffee across the street and recording everything happening around the bank for 3 months in a row just a coffee drinker? Then…. why is your cyber security team considering phishing messages as ‘just phishing’? Have you never thought of the possibility that someone could have been planning an attack on your organisation for the past 3 to 12 months, and this phishing message is their final blow?
So let me paint a different picture of phishing for you.
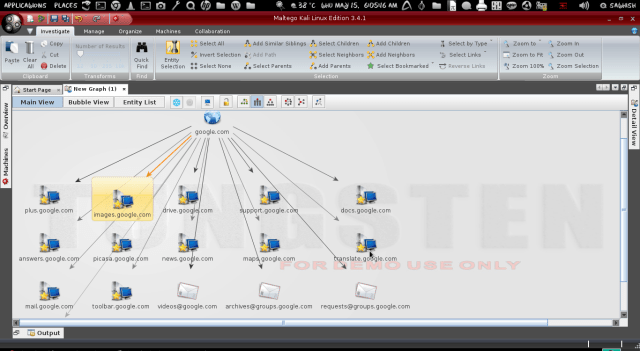 The image above represents research. The research of an organisation within a tool called Maltego. See the central node, paterva.com? It represents the central target of this research, and all the nodes expanding from it – represent points of interest. One of these points will be a person – a person the criminals find through LinkedIn, Facebook or other means – someone who will represent an entry point into your organisation, someone, who will fill their corporate username and password into a carefully created web page, made with care and love just for them.
The image above represents research. The research of an organisation within a tool called Maltego. See the central node, paterva.com? It represents the central target of this research, and all the nodes expanding from it – represent points of interest. One of these points will be a person – a person the criminals find through LinkedIn, Facebook or other means – someone who will represent an entry point into your organisation, someone, who will fill their corporate username and password into a carefully created web page, made with care and love just for them.
I believe it is time for us, after years of ignoring the problem and making it look insignificant, to change our perception and start seeing the real picture behind phishing. If you notice that your bank is being monitored for the past 3 months, you will be worried. Should you be worried if your employees start receiving phishing messages? Well… let us consider that an attack group only sends a phishing message after their research process is complete, after they have mapped out your organisation much better than the image above, when they have labeled all your weak points, when they know exactly how are they going to use the stolen credentials. This happens after they know exactly which information they are going to take from your company and what they will do with it. So phishing is not the fake web page nor the e-mail you receive. It is an indicator that someone might have just completed twelve months of research on you and is ready to deliver their final blow – one that you might not even notice until your most valuable information is no longer confidential – and probably in the hands of someone else.
I hope this article wakes you up. I hope you share it with whoever needs to know about it – and I hope that your view of phishing is a little bit more realistic after reading it.