Atlant Security © 2024. All rights reserved
This article aims to be vendor-neutral; this is why the image below does not list any company or vendor names. But it gives you a good idea of how many defensive measures and defensive categories have to be taken care of to establish solid cloud security.
Cloud security is the combination of people, processes, technology, and infrastructure providing secure and always available services without reliance on internal corporate infrastructure.
Suppose you use a locally hosted server in your network to provide a service to internal or external customers. In that case, you will need to apply one set of measures to protect this server (or a cluster of servers) from insider or outsider threats. You will also need to ensure proper access controls and network risk mitigation measures.
If you use a set of services hosted at a cloud provider to deliver the same service to internal or external customers, you will need to implement an entirely different set of security controls. The cloud provider already did most of the work to ensure physical and network security requirements.
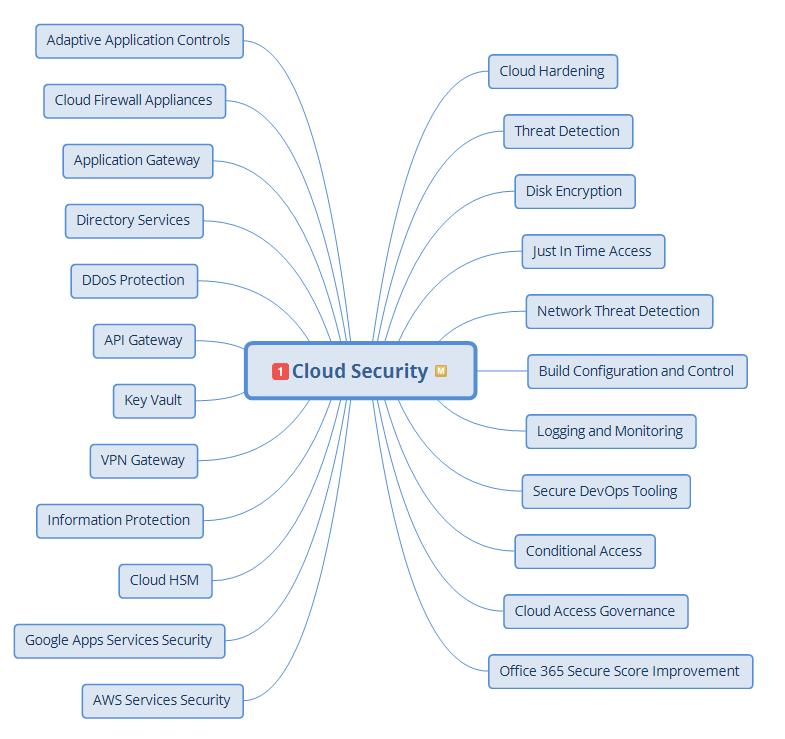
There are three sides to cloud security: the client, the provider, and the cloud infrastructure side.
For example:
You may want to provide a cloud service to your clients: in that case, you are the cloud service provider. If you host your product in Microsoft’s Azure, Google’s Cloud, or Amazon’s AWS, they would be your infrastructure provider. The ones accessing and using your cloud service would constitute your clients.
All three stakeholders from the example above are required to perform different steps to protect themselves.
The clients need to access your cloud service from secure, non-compromised computers and maintain good credential hygiene: use a password manager, unique passwords, and 2-factor authentication.
The infrastructure providers – Google, Amazon, or Microsoft, would need to protect their servers, operating systems, networks and ensure adequate access controls for their engineers. The infrastructure providers have to provide all necessary security controls to their customers.
As the service provider who hosts their service in the cloud, you must use all the infrastructure providers’ security controls in the best way possible.
Cloud security controls are entirely different from the ones applied inside an internal network. Identity and access management is the most crucial set of security controls when defending cloud services.
It includes:
These security controls must be present on the provider and the user side. If the cloud service presents all these security controls, but you do not fully configure and utilize them, these controls are effectively missing.
When all stakeholders utilize all security controls available to them in the best way possible, we can say that we have cloud security.
In 2021 most companies still rely on internal infrastructure and are cautious towards cloud services because they cannot imagine how to ensure their security in the cloud.
Pros and cons of hosting your data and services in the cloud
Startups and progressive companies generally choose to utilize a cloud provider to deliver scalable and secure services to their customers. According to Statista, the market penetration of cloud services on average in multiple business sectors is 36% and growing. That does mean that 64% of businesses still rely on their infrastructure, but that number is rapidly declining. In 2015 it was 76%.
Pros
Cons
Pros and cons of hosting your data and services on-premise
There are some clear advantages of hosting your data in your own data center, but there are also some disadvantages.
Pros
Cons
If we look at the requirements to ensure traditional infrastructure is secure, they look something like this (clickable link):
Cloud security, on the other hand, is much more complicated than on-premise infrastructure in some situations. In some, because hosting a simple application or dataset could be both secure and straightforward.
Every one of the major cloud providers – Google, Microsoft, Amazon AWS, Baidu, Yandex, among many others in most large countries – has an entirely different set of security measures in place for every single one of their cloud offerings.
Amazon’s Identity and Compliance page list hundreds of whitepapers, training materials, and instructions to protect the hundreds of offerings in AWS.
Microsoft has two major parts in its cloud offering – Azure (similar in volume and capabilities to AWS) and Microsoft 365, the office and collaboration suite in the cloud by Microsoft.
Their cloud security documentation is even more detailed, covering the complexity of each cloud service and the efforts required to secure it.
Google’s Cloud Security and Identity documentation page are just as detailed as the previous two. It may take one engineer years to learn the intricacies of a single cloud provider’s security capabilities, by which time everything will have changed, and they would have to learn again.
Traditional security was easier.
When IT administrators had to install and maintain desktops and servers, their view of the requirements to protect those desktops and servers was relatively unambiguous.
Since the year 2004, cybercrime has grown exponentially, along with the attackers’ capabilities and their skills to compromise traditional IT infrastructure. Since then, every year, the number of hacked organizations grows at an astounding rate. We could compare it to compound interest rates for those coming from the financial world.
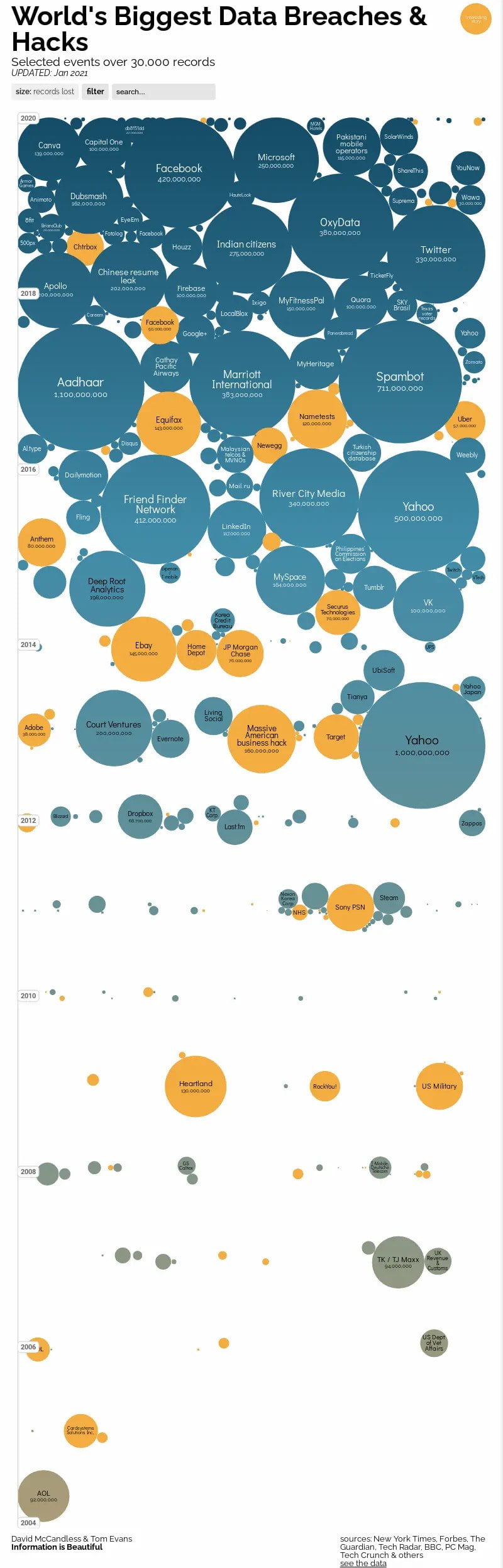
The imbalance between the knowledge and skills of regular IT administrators and the global collective experience of hackers on how to bypass traditional IT security reached a point where traditional on-premises IT security cannot hold them any longer.
One average company with one set of IT administrators and perhaps one or two security engineers cannot resist the global offensive of hundreds of thousands of hackers globally, each with a different skillset and tools.
Cloud security makes it easier to survive in the digital world.
Each global cloud provider has thousands of security engineers at hand, working together day and night to build scalable and resilient systems. These systems are capable of resisting threats that change every second. Traditional IT and IT security teams cannot operate at such a fast pace. We face the immutable imbalance of economies of scale when discussing the topic of conventional vs. cloud security.
According to Forbes, there are more than 2300 cloud security companies on the market, and the cloud security market grows exponentially with the cloud security offers of companies worldwide.
These categories define the cloud security market:
Amazon launched its AWS service back in 2006, being a pioneer among the world’s tech giants.
Google followed on April 7th, 2008, with its GCP offering.
Microsoft Azure launched on February 1st, 2010. Since June 28th, 2011, when Office 365 launched (now known as Microsoft 365), Microsoft steers primarily in the direction of developing its cloud services.
The majority of services we all use today run in one of the three cloud providers listed above.
Logically, when talking about the cloud security market, we have to accept that most data and services depend on their security on either Microsoft, Google, or AWS.
Most security companies also shifted towards offering cloud-based solutions. Endpoint security vendors went into the cloud security space after inevitably failing to provide an adequate defense with just their on-premises capabilities. A single antivirus engine on a single computer can never act on the sheer global threat intelligence volume as well as a thousand servers running in the cloud can.
The same reason is valid for cloud-based security vendors offering threat investigation, cloud firewalls, cloud-based vulnerability scanners, and many others.
The cloud security market is estimated to be worth 12.73 Billion USD by 2022, growing from just 4.09 billion in 2017.
The spending to protect cloud assets is estimated to increase by 250.3%.
These numbers only show that the market for cloud security is just beginning to grow, and the trend is clearly against on-premise infrastructure.
As mentioned earlier in this article, there are more than 2300 cloud security companies globally, and their number keeps growing.
Atlant Security is one of the cloud security companies focusing on consulting and virtual CISO services. These services will help you ensure your migration to the cloud or your presence in a cloud-centric world remains secure.
Cloud security companies bridge the gap in defense measures open in significant cloud service providers’ current offerings. For example, Microsoft Azure does not provide web or API firewalls, and you must find a cloud security vendor who does.
Cloud security providers
Cloud Security Services
Cloud security assessment
Cloud security testing comes in many flavors. There is regular security audit testing which enumerates all settings and finds the ones in need of improvement. There are also numerous ways of penetration testing a cloud environment: white box, grey box, and black box cloud penetration testing. There is a vulnerability assessment against the services you have running in the cloud. API penetration testing is part of the many penetration testing, among web penetration testing, etc.
While most people imagine penetration testing to be the only viable way, others see a plethora of possibilities to test the security of your cloud infrastructure.
As cloud environments consist of Iaas (infrastructure as a service), PaaS (platform as a service), and Saas (software as a service), each of these has its own sub-sets of services and tests to ensure security.
Cloud security testing: knowledge evaluation
Are the people using and administering the Cloud trained well to defend it? Did you test their knowledge?
This may be especially applicable to old-school IT administrators tasked with migrating your data to the Cloud.
Which are the most critical cloud security best practices a company must follow to avoid a breach?
There is a simple and a complicated answer to this question.
The simple answer is: follow the documentation and security best practices listed by your cloud provider. We have already listed them with links to the documentation of the three major cloud providers, AWS, Microsoft, and Google.
But following documentation is one thing; prioritizing your work to reflect your highest risks and your resources to protect yourself is another.
You cannot just blindly go and apply every single security mitigation available at a cloud provider because you could seriously hurt your business and its availability.
You may also end up spending more time and resources than you could safely allocate if you don’t prioritize based on real-life risk.
You can’t fully secure your cloud environment without taking care of the basics first. That is why you will still need to focus on ISO 27001/ISO 27002, as they cover fundamental concepts such as your incident response procedures, disaster recovery and backups, access management procedures, and much more.
On top of the fundamentals, you will need to adopt additional cloud security standards with specific requirements to cloud infrastructure.
Figure 1 Source: NIST 500-291, NIST Cloud Computing Standards Roadmap
As per the figure above, the three kinds of cloud providers – Software as a Service, Platform as a Service, and Infrastructure as a Service, require different security controls.
There are two global schools of thought when it comes to cloud security standards: NIST and ISO.
As a cloud security consulting company, Atlant Security recommends that your team sides with NIST recommendations, as they are more practical and implementable than the more bureaucratic ISO set of cloud security standards. Another major difference: just reading the ISO standards documentation will cost you hundreds of dollars each. NIST publications are free to access.
The way to read and apply NIST security guidelines is to transform their advice and requirements into checklists and gradually implement them as if you were going through a year-long, complex project.
The US-based NIST (National Institute of Standards and Technology) issued several core documents which can be used to standardize your approach to security:
NIST has hundreds of smaller publications and articles on cloud security, but those are the core ones we would like to focus on.
ISO Cloud security standards:
You may be unhappy with what Azure Sentinel offers in security monitoring and might go for a different cloud security monitoring vendor.
Cloud security and compliance
Cloud Security Solutions
cloud security strategy
It would take several months of full-time reading, 8 hours a day, for a systems engineer just to read all the security documentation of a single cloud security vendor such as Microsoft Azure or Amazon AWS.
Sending your on-premises systems administrator to secure your newly established cloud environment without the appropriate rigorous training would be a wrong move. It will most certainly end in disaster.
Either hire cloud security professionals like Atlant Security to help you or provide your team with the right training for the job.
While the number of cloud security companies grows steadily, the number of jobs focusing on cloud security grows exponentially due to the increase in complexity and the rapid increment of services offered by the same companies.
The demand for cloud security jobs is growing.
We observe a growing number of previously non-existing job roles pop up in the cloud security market: Cloud security engineers, architects, monitoring experts, and many others.
No matter if you are a fresh graduate or a seasoned IT expert with decades of experience, all you need to do to get a cloud security job is to spend a few focused months learning the basics, practice with a free account and apply.
Issues with cloud security
Cloud security challenges
Cloud security concerns
Since your data, servers, and applications moved to the cloud, their threats are no different from what they were in your own data center.
Identity and access management misconfigurations and malpractices are the main source of threats to your cloud security.
Small cloud providers are much riskier.
In addition to the threats inherent to access and identity management, you also have threats for the cloud service itself. A major cloud service provider in France, OVH, had their entire data center burn down in March 2021 – which affected their backups, too. Many of their customers lost their entire websites, databases, and backups in that fire. If they didn’t do any off-site backups, then that data is gone forever.
This cannot happen with major cloud providers, such as Azure, Amazon, and Google, because their data centers are distributed worldwide and have data replication. But this regional cloud service provider (OVH) remains an example of how fragile smaller cloud service providers are.
Your team’s knowledge about cloud security
One of the biggest risks when migrating your infrastructure to the cloud (and if you are reading this, you are most likely just in the planning phase) is the lack of knowledge and understanding of how the Cloud differs from on-prem infrastructure.
There is a huge difference between just having and administering a bunch of servers and network devices in your own network and the kind of web-based interfaces and access management which exists in the Cloud.
A major risk would be installing a few virtual machines in a cloud environment and forgetting to protect all access to the main administrative interface of all your cloud services. You may secure the virtual machines all you want – if a hacker obtains access to your cloud management, it will still be ‘game over.
Exposing secrets not meant to become public
Your development or IT teams can unwillingly expose secrets such as passwords or configuration files, or even entire databases, to the public. It becomes much easier to make such mistakes in cloud environments, especially when the team learns how to use the particular cloud service and protect it.
An IT Security audit is an audit of how resilient are your information technology systems to attack or human error. Its scope depends on the size of the company and its objectives. An IT security audit might mean a quick assessment of a few systems or a comprehensive review of your on-premise and cloud infrastructure.
We audit the controls in place (or their absence). These controls might be administrative, or in other words, the practices employed by your administrators. They could also be technical or even physical.
Physical security controls are not necessarily related to the prevention of theft by an outside party. Proper cooling of the server room to prevent overheating and critical damage is also a physical security control. Preventing people from plugging in various unknown devices in servers and computers can also be seen as a physical security control.
Atlant Security © 2024. All rights reserved